Confidentiality Techniques: Encryption, Decryption, and Hashing
Learn how encryption, decryption, and hashing techniques can be utilized to ensure data confidentiality and security. Discover the importance of safeguarding sensitive information such as credit card numbers through encryption methods. Understand the role of symmetric and asymmetric key encryption in protecting data from unauthorized access.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
ENCRYPTION, DECRYPTION, AND HASHING
Encryption, Decryption, And Hashing for Confidentiality At times, we may have situations where we must store data in a table. but also we want to keep that data confidential, even if one has access to retrieve that data. say we need to store a user s credit card number.
Encryption, Decryption, And Hashing for Confidentiality If we were to store the number, any user, role, or view that has access to that data can access the stored credit card number. We cannot rely on user or role column-level privileges alone for a security measure here, because we need to allow each user.
Encryption, Decryption, And Hashing for Confidentiality access to the column in order to access their credit card column value. we cannot completely deny a user access to that column. to protect confidential data in the event of a compromised privileged account or a malicious user that is able to obtain the privilege to access and see the data.
Encryption, Decryption, And Hashing for Confidentiality In these situations, we cannot store the data in raw or plaintext form. otherwise, a user, role, or view accessing the data can clearly see the confidential data. If we were to store the credit card number in plaintext form, any user, role, or view that has access to that data can clearly see the stored number.
Encryption, Decryption, And Hashing for Confidentiality We need a way in which we can employ confidentiality so unauthorized user or role gains access to the credit card data, we do not want the number to be revealed. that, should an
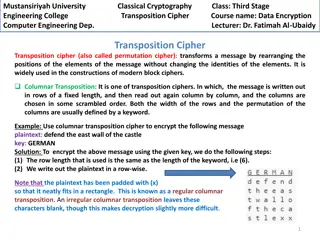
Encryption, Decryption, And Hashing for Confidentiality The typical solution to this confidentiality problem is to employ techniques that scramble the data into ciphertext. encryption or There symmetric key and asymmetric key. are two forms of encryption:
Encryption, Decryption, And Hashing for Confidentiality Symmetric key (or shared key) encryption uses the same key (such as a password or passphrase) to encrypt as well as decrypt. In other words, for the decryption of ciphertext to be successful, one must provide the same key that was used to encrypt that ciphertext.
XOR cypher (vernam cypher) E.g., the string "Wiki" (01010111 01101001 01101011 01101001 in 8- bit ASCII) can be encrypted with the repeating key 11110011 as follows:
Encryption, Decryption, And Hashing for Confidentiality with asymmetric (or public key) encryption, one key is used for encryption and another key must be used for decryption. The two keys are generated beforehand as a key pair, such that one key encrypts and other decrypts. asymmetric key encryption by using one key (typically a user s public key) to encrypt and the corresponding other key (typically the same user s private key) to decrypt.
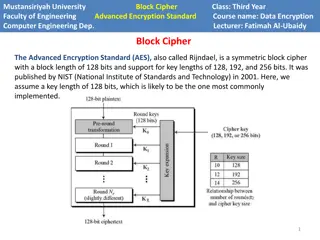
Encryption, Decryption, And Hashing for Confidentiality We will demonstrate encryption and decryption using the advanced encryption standard (AES). which is widely accepted as the most secure encryption approach because AES ciphertext is virtually impossible to convert back to plaintext without the proper key. To encrypt data in our DBMS, we use the AES_ENCRYPT function, whose basic syntax.
Encryption, Decryption, And Hashing for Confidentiality The first argument is the plaintext data in string form. the second argument is the encryption key, such as a password or passphrase. The function returns the generated ciphertext.
Encryption, Decryption, And Hashing for Confidentiality We will use symmetric encryption to encrypt some plaintext (in this case my secret data ) with a simple password (in this case mykey ).
Encryption, Decryption, And Hashing for Confidentiality The AES_ENCRYPT function returns the ciphertext as a binary string or a sequence of byte values, not a character string. This is because some AES ciphertexts may not be representable as alphanumeric symbols. As such, the SELECT statement in Figure shows the ciphertext in hexadecimal or base 16 formats. We consider that a hexadecimal symbol consists of the digits 0 to 9 and the letters A to F, allowing 16 possible values per symbol, or base 16.
Encryption, Decryption, And Hashing for Confidentiality Decryption The distinction between the ciphertext as a binary string and a character is important because we must provide that ciphertext as a binary string to correctly decrypt it back to the original plaintext. One way we can do that is to give the given ciphertext hexadecimal representation with the 0x prefix but no quotes, which is the approach we will use to decrypt. In this manner, we can decrypt the ciphertext that we just created and see the resulting plaintext.
Encryption, Decryption, And Hashing for Confidentiality Decryption To decrypt the ciphertext back to the original plaintext, we can use the AES_DECRYPT function, whose basic syntax to decrypt is given in Figure.
Encryption, Decryption, And Hashing for Confidentiality
Encryption, Decryption, And Hashing for Confidentiality Decryption AES_DECRYPT also returns a binary string and not a character string, so in order to see the character representation of the resulting plaintext, we must convert the result into a character format. We can accomplish that task with the CAST function, which in this situation takes as an argument the binary string result generated by AES_DECRYPT, and then we specify AS CHAR to convert that argument into a character format.
Encryption, Decryption, And Hashing for Confidentiality Hashing A hash is a scrambled representation of data, which may sound like encryption but rather is a one-way scrambling, in that a hash cannot be unscrambled back to the original data. By providing a hash form of the password or passphrase during encryption, we can encrypt with an additional level of security compared to encrypting with the password or passphrase alone. This further protects the encrypted ciphertext (password or passphrase) against attacks that involve password guessing or password cracking.
Encryption, Decryption, And Hashing for Confidentiality Hashing There are a number of hashing methods that we can use, although the one considered to be most secure is the secure hash algorithm (SHA). There are actually three SHA versions: SHA1 (sometimes called just SHA), SHA2, and SHA3. Currently Oracle, MySQL, and MariaDB natively support SHA1 and SHA2.
Encryption, Decryption, And Hashing for Confidentiality Hashing SHA2 is more secure than SHA1 and, of these two, should be used when available. We can generate an SHA2 hash into 256, 384, or 512 bits (or 64, 128 hexadecimal symbols), and we can represent that as SHA-256, SHA- 384, or SHA-512, respectively. The larger the number of bits, the more secure the hash value against two different plaintext data sets hashing to the same value (known as a collision), as well as against reversing the hash value back to the plaintext.
Encryption, Decryption, And Hashing for Confidentiality Hashing To generate an SHA2 hash of 256 bits, we can issue the SHA2 function with two arguments. The first argument is the plaintext and the second argument is the number of bits for the hash, in this case 256.
Encryption, Decryption, And Hashing for Confidentiality Hashing Figure generates and shows the SHA2 hash value of 256 bits for the plaintext myplaintext . In this example, the hash value is the sequence of 64 hexadecimal symbols that starts with 8cde. Because SHA2 returns a character string and not a binary string, the result is not prefixed with 0x.
Encryption, Decryption, And Hashing for Confidentiality Hashing To see the resulting ciphertext that combines SHA2 256 bit hashing with a key to make the previous encryption example more secure, we can issue the statement given in Figure.
Encryption, Decryption, And Hashing for Confidentiality Hashing Notice that we are providing the hash value of the key rather than the key itself. And recall that AES_ENCRYPT returns a binary string, hence the resulting ciphertext is prefixed with 0x
Encryption, Decryption, And Hashing for Confidentiality Hashing To decrypt ciphertext that was encrypted with a hashed key. we must also provide the same hashed key as the decrypt key. The figure demonstrates how we can decrypt the ciphertext that we just encrypted with the hashed key and see the resulting plaintext.
Encryption, Decryption, And Hashing for Confidentiality Hashing
Encryption, Decryption, And Hashing for Confidentiality Hashing