Cryptographic Algorithms Used in Data Encryption
Explore the classification of cryptographic algorithms based on key usage, including Secret Key Cryptography (SKC), Public Key Cryptography (PKC), and Hash Functions. Learn about Feistel Cipher, Block Cipher, and the structure of Feistel Cipher proposed by Feistel for creating block ciphers efficiently.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
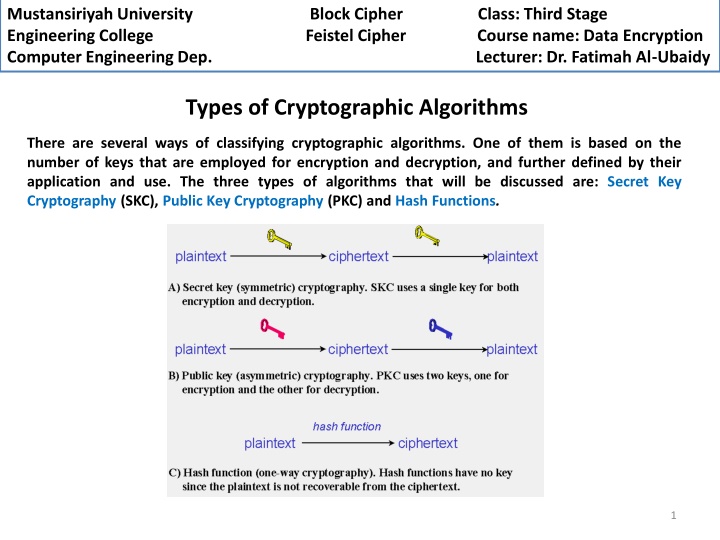
Mustansiriyah University Engineering College Feistel Cipher Computer Engineering Dep. Lecturer: Dr. Fatimah Al-Ubaidy Block Cipher Class: Third Stage Course name: Data Encryption Types of Cryptographic Algorithms There are several ways of classifying cryptographic algorithms. One of them is based on the number of keys that are employed for encryption and decryption, and further defined by their application and use. The three types of algorithms that will be discussed are: Secret Key Cryptography (SKC), Public Key Cryptography (PKC) and Hash Functions. 1
Mustansiriyah University Engineering College Feistel Cipher Computer Engineering Dep. Lecturer: Dr. Fatimah Al-Ubaidy Block Cipher Class: Third Stage Course name: Data Encryption Secret Key Cryptography Secret key cryptography uses a single key for both encryption and decryption; also called symmetric encryption. Primarily used for privacy and confidentiality. Because a single key is used for both functions, secret key cryptography is called symmetric encryption. With this form of cryptography, it is obvious that the key must be known to both the sender and the receiver and it is the secret. The biggest difficulty with this approach is the distribution of the key. Secret key cryptography schemes are generally categorized as being either stream ciphers or block ciphers. 2
Mustansiriyah University Engineering College Feistel Cipher Computer Engineering Dep. Lecturer: Dr. Fatimah Al-Ubaidy Block Cipher Class: Third Stage Course name: Data Encryption Block Cipher (1) Block Cipher is an encryption/decryption scheme in which a block of plaintext is treated as a whole and used to produce a ciphertext block of equal length. Its structure consists of a number of identical rounds of processing. In each round, a substitution is performed on one half of the data being processed, followed by a permutation that interchanges the two halves. The original key is expanded so that a different key is used for each round. Substitution: Each plaintext element or group of elements is uniquely replaced by a corresponding ciphertext element or group of elements. Permutation: A sequence of plaintext elements is replaced by a permutation of that sequence such that the order in which the elements appear in the sequence is changed. Confusion: refers to making the correlation between the key and the ciphertext as complex as possible (each character of the ciphertext should depend on several parts of the key). This is achieved by the use of a complex substitution algorithm. Diffusion: complicates the statistics of the ciphertext, and makes it difficult to discover the key. This is achieved by having each plaintext digit affect the value of many ciphertext digits. (Permutation) 3
Mustansiriyah University Engineering College Feistel Cipher Computer Engineering Dep. Lecturer: Dr. Fatimah Al-Ubaidy Block Cipher Class: Third Stage Course name: Data Encryption Feistel Cipher The Feistel Cipher: Feistel proposed that we can approximate the ideal block cipher by utilizing the concept of a product cipher, which is the execution of two or more simple ciphers in sequence. The essence of the approach is to develop a block cipher with a key length of k bits and a block length of n bits, allowing a total of possible 2n transformations. FEISTEL cipher structure: The inputs to the encryption algorithm are a plaintext block of length 2w bits and a key K. (1) The plaintext block is divided into two halves, L0 and R0. (2) The two halves of the data pass through nrounds of processing and then combine to produce the ciphertext block. (3) Each round i has as inputs Li-1 and Ri-1 derived from the previous round, as well as a subkey Ki derived from the overall K. In general, the subkeys Ki are different from K and from each other. (4) A substitution is performed on the left half of the data. This is done by applying a round function F to the right half of the data and then taking the exclusive-OR of the output of that function and the left half of the data. (5) A permutation is performed that consists of the interchange of the two halves of the data. 4
Mustansiriyah University Engineering College Feistel Cipher Computer Engineering Dep. Lecturer: Dr. Fatimah Al-Ubaidy Block Cipher Class: Third Stage Course name: Data Encryption Feistel Encryption and Decryption 16 rounds 5
Mustansiriyah University Engineering College Feistel Cipher Computer Engineering Dep. Lecturer: Dr. Fatimah Al-Ubaidy Block Cipher Class: Third Stage Course name: Data Encryption Feistel Block Cipher The parameters and design features of Feistel network: Block size: Larger block sizes mean greater security but reduced encryption/decryption speed for a given algorithm. The greater security is achieved by greater diffusion. Traditionally, a block size of 64 bits has been considered a reasonable trade-off. Key size: Larger key size means greater security but may decrease encryption/decryption speed. The greater security is achieved by greater resistance to greater confusion. Key sizes of 64 bits or less are now widely considered to be inadequate, and 128 bits has become a common size. Number of rounds: A single round offers inadequate security but that multiple rounds offer increasing security. A typical size is 16 rounds. Subkey generation algorithm: Greater complexity in this algorithm should lead to greater difficulty of cryptanalysis. Round function F: Greater complexity generally means greater resistance to cryptanalysis. Fast software encryption/decryption: In many cases, encryption is embedded in applications in such a way as to preclude a hardware implementation. Accordingly, the speed of execution of the algorithm becomes a concern. Ease of analysis: We would like to make our algorithm as difficult as possible to cryptanalyze. 6






















