Cryptography and Block Ciphers: Understanding LFSR, DES, 3DES, AES
Explore the world of cryptology, cryptanalysis, symmetric, and asymmetric cryptography. Dive into the concepts of stream and block ciphers, LFSR, DES, 3DES, and AES encryption algorithms. Learn about key lengths, cycle lengths, and the security aspects of cryptographic systems.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
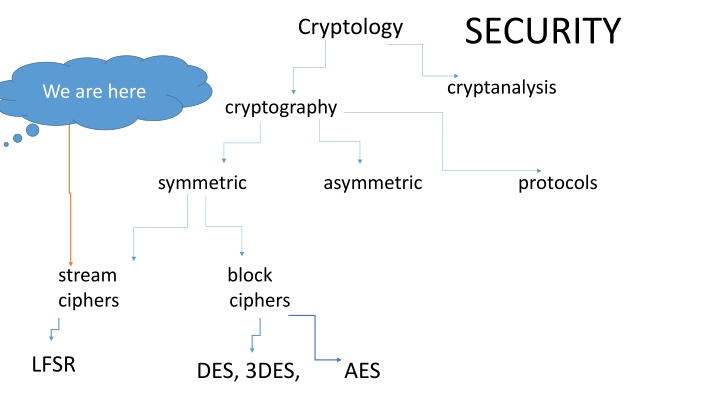
SECURITY Cryptology cryptanalysis We are here cryptography symmetric asymmetric protocols stream block ciphers ciphers LFSR DES, 3DES, AES
You have an LFSR with 5 FF s A starting seed of 0x1C A feedback vector of 0x0a 1. Show one full cycle of key bits. 2. What is the length of the cycle? 3. What is the maximum possible length for an LFSR with 5 FF s?
SECURITY Cryptology cryptanalysis cryptography symmetric asymmetric protocols We are here stream block ciphers ciphers LFSR DES, 3DES, AES
Block Ciphers Deterministic algorithms which act on fixed size chunks of bits call blocks Transform specified by a symmetric key
Claude Shannon Claude Shannon, a researcher at AT&T Bell Laboratories, is the father of Computer Science. He completed his masters thesis "A Symbolic Analysis of Relay and Switching Circuits," at age 22, which was called "possibly the most important, and also the most famous, master's thesis of the century. - Harvard University Professor Howard Gardner. Boolean algebra realized using electromagnetic relays data compression early notions of chatGPT, inter alia cryptology information theory
cryptographic algorithm (cipher) a mathematical function plus a key to en/decrypt The same plaintext encrypts to different ciphertext with different keys.
Secrecy of the key and strength of the cipher determine the security Not is it secure? Yes/no , but rather how long will it take to break it? The answer is expressed as a unit of time. Cryptosystem - cryptographic algorithm, plus all possible keys and all the protocols that make it work comprise a cryptosystem (PGP)
Symmetric-key is fast useful for encrypting data that is not to be transmitted But, secure key distribution is the gotcha We still need a secure channel to tell the other party the key
Block Cipher Key K bits long | v Chunk of n encrypted bits Chunk of n cleartext bits Most are iterated meaning we do it over and over in a round with different keys, each derived from the original
Combine substitutions and transpositions (permutations) crypto-quote and jumble puzzles Iterated cipher, carried out in rounds each round uses a different sub-key derived from the original Rounds alternate (DES - Horst Feistel, hence Feistel network )
Combine substitutions and transpositions crypto-quote and jumble puzzles transposition
Combine substitutions and transpositions crypto-quote and jumble puzzles substitution
Iterated cipher, carried out in rounds each round uses a different sub-key derived from the original
DES, 3DES, at a time An early way to visualize the Rounds of encryption for DES from Horst Feistel, hence Feistel network
Substitution-permutation block cipher several alternating rounds of substitution and permutation Substitution, change symbol Substitution, change symbol A more current symbolic mechanism to visualize rounds carried out during the execution of an encryption algorithm permutation, shuffle symbols Iterated cipher, carried out in rounds each round uses a different sub-key derived from the original --wikipedia
A substitution box substitutes a small block of input bits with another block of output bits. 1-1 so it can be decrypted A permutation box takes the outputs of all the S-boxes of one round, permutes the bits, and feeds them into the S-boxes of the next round. Iterated cipher, carried out in rounds each round uses a different sub-key derived from the original
Confusion refers to making the relationship between the key and the ciphertext as complex and as involved as possible Diffusion refers to the property that redundancy in the statistics of the plaintext is "dissipated" in the statistics of the ciphertext.
Confusion a primary mechanism is substitution (cryptoquote) Diffusion - primary mechanism is transposition (jumble) A required property is that a small change in cleartext, yields a large change in encrypted text Ideally, if you flip an input bit, we would like a 50-50 chance that each output bit flips an avalanche of changes
Bad: cleartext ciphertext 0x99 0x26 0x11 0xcd 0x00 0x67 0x8e 0xee 0x30 0x02 0x44 0xc4 0x23 0x71 0xa0 0x00 0x31 0xfa 0x29 0x44 0x51 0x10 0x00 0xab cleartext ciphertext 0x99 0x26 0x11 0xcd 0x00 0x67 0x8e 0xef 0x30 0x02 0x44 0xc4 0xa3 0x71 0xa0 0x00 0x31 0xfa 0x29 0x44 0x51 0x10 0x00 0xab Causes a single bit to change in the ciphertext 1110 becomes 1111 A single bit changed: 0010 becomes 1010
Good: cleartext ciphertext 0x99 0x26 0x11 0xcd 0x00 0x67 0x8e 0xee 0x30 0x02 0x44 0xc4 0x23 0x71 0xa0 0x00 0x31 0xfa 0x29 0x44 0x51 0x10 0x00 0xab cleartext ciphertext 0xc0 0x56 0xe2 0x80 0xdd 0xdd 0x19 0xb1 0x30 0x82 0x4c 0x25 0xa3 0x71 0xa0 0x00 0x31 0xfa 0x29 0x44 0x51 0x10 0x00 0xab Causes many changes A single bit changed: 0010 becomes 1010
1. Confusion a primary mechanism is substitution (cryptoquote) 2. Diffusion - primary mechanism is transposition (jumble) Substitution and transposition are most common, but AES uses linear transformations
Algorithm Description Key Length Block cipher developed by Schneier Blowfish 1-448 bits DES adopted as a U.S. government standard in 197756 bits DES Block cipher developed by Massey and Xuejia lots of them IDEA 128 bits MARS AES finalist developed by IBM 128-256 bits Block cipher developed by Rivest Stream cipher developed by Rivest RC2 1-2048 bits RC4 1-2048 bits Block cipher developed by Rivest and published in 1994 RC5 128-256 bits AES finalist developed by RSA Labs RC6 128-256 bits NIST selection for AES, developed by Daemen and Rijmen Rijndael 128-256 bits AES finalist developed by Anderson, Biham, and Knudsen Serpent 128-256 bits A three-fold application of the DES algorithm Triple-DES 168 bits AES candidate developed by Schneier Twofish 128-256 bits
Data Encryption Standard - DES First cryptography in the public space proposed by IBM/NSA in 1974 U.S. government standard in 1977 ANSI standard in 1981 Gov t standard until around 2000 Very widely distributed, implemented, studied
Data Encryption Standard - DES block cipher using a 56-bit key strong algorithm, but limited by key length Unsecure today, hardware to defeat it emerged in 1988 3DES triple DES, still considered secure most widely used https://www.youtube.com/watch?v=Sy0sXa73PZA&t=1s
56 bit key - give openssl an 8 character key, 7 bits from each == 56bits DES 64 encrypted bits and write out the 8 corresponding cipher text bytes 64 bits clear so, read the file 8 bytes at a time Symmetric keys 16 rounds, all of which are the same Different subkey in each round
openssl(1) libcrypt.a(3) e.g. encrypt & decrypt with DES encrypt file.clr, save encrypted version as file.enc openssl des pbkdf2 -e -a -in file.clr -out file.enc decrypt file.enc, print clear text to the terminal openssl des pbkdf2 d a in file.enc out /dev/tty
openssl(1) libcrypt.a(3) e.g. encrypt & decrypt with DES encrypt file.clr, save encrypted version as file.enc openssl des pbkdf2 -e -a -in file.clr -out file.enc decrypt file.enc, print clear text to the terminal openssl des pbkdf2 d a in file.enc out /dev/tty