Data Encryption in Classical Cryptography: Substitution and Playfair Ciphers
Explore the concepts of substitution ciphers like the famous Caesar cipher and the advanced Playfair cipher in classical cryptography. Understand the encryption and decryption algorithms, key tables, and security measures involved. Dive into the world of data encryption in computer engineering.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
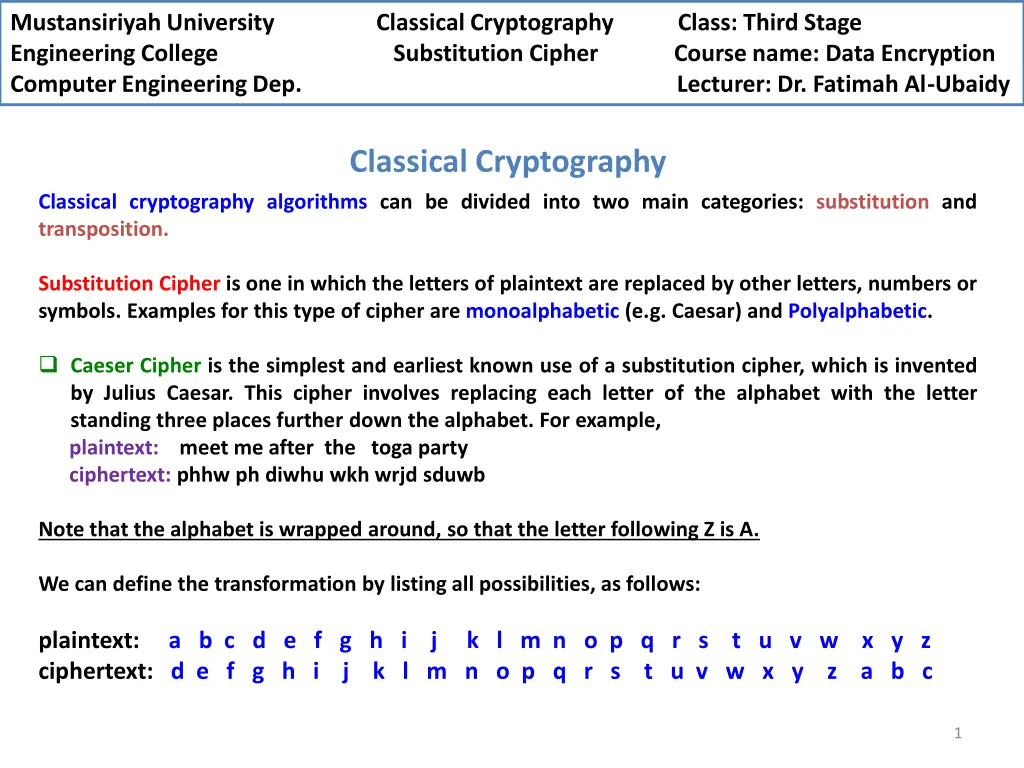
Mustansiriyah University Engineering College Substitution Cipher Course name: Data Encryption Computer Engineering Dep. Lecturer: Dr. Fatimah Al-Ubaidy Classical Cryptography Class: Third Stage Classical Cryptography Classical cryptography algorithms can be divided into two main categories: substitution and transposition. Substitution Cipher is one in which the letters of plaintext are replaced by other letters, numbers or symbols. Examples for this type of cipher are monoalphabetic (e.g. Caesar) and Polyalphabetic. Caeser Cipher is the simplest and earliest known use of a substitution cipher, which is invented by Julius Caesar. This cipher involves replacing each letter of the alphabet with the letter standing three places further down the alphabet. For example, plaintext: meet me after the toga party ciphertext:phhw ph diwhu wkh wrjd sduwb Note that the alphabet is wrapped around, so that the letter following Z is A. We can define the transformation by listing all possibilities, as follows: plaintext: a b c d e f g h i j k l m n o p q r s t u v w x y z ciphertext: d e f g h i j k l m n o p q r s t u v w x y z a b c 1
Mustansiriyah University Engineering College Substitution Cipher Course name: Data Encryption Computer Engineering Dep. Lecturer: Dr. Fatimah Al-Ubaidy Classical Cryptography Class: Third Stage Let us assign a numerical equivalent to each letter: Then the encryption algorithm Ek can be expressed as follows. For each plaintext letter P, substitute the ciphertext letter C: Ci= Ek(Pi) = (Pi+ 3) mod 26 Not that We define a mod n to be the remainder when a is divided by n. For example, 11 mod 7 = 4. A shift may be of any amount, so that the general Caesar algorithm is Ci= Ek(Pi) = (Pi+ K) mod 26 where Kis the key, whichtakes on a value in the range 1 to 25. The decryption algorithm Dk is Pi= Dk(Ci) = (Ci- K) mod 26 2
Mustansiriyah University Engineering College Substitution Cipher Course name: Data Encryption Computer Engineering Dep. Lecturer: Dr. Fatimah Al-Ubaidy Classical Cryptography Class: Third Stage Substitution Cipher Playfair Cipher: it is a symmetric multiple-letter encryption, which treats a pair of letters in the plaintext as a single unit and translate them into a different unit in the ciphertext. - The playfair cipher starts with creating a key table. The key table is a 5 5 grid of letters that will act as the key for encrypting the plaintext. Each of the 25 letters must be unique and one letter of the alphabet (usually Q) is omitted from the table. - The Playfair cipher uses a few simple rules for encryption as follows: 1) If both letters are in the same column, take the letter below each one (going back to the top if at the bottom), 2) If both letters are in the same row, take the letter to the right of each one (going back to the left if at the farthest right), 3) If neither of the preceding two rules are true, form a rectangle with the two letters and take the letters on the horizontal opposite corner of the rectangle, 4) If both letters are the same (or only one letter is left), add an "X" after the first letter. 3
Mustansiriyah University Engineering College Substitution Cipher Course name: Data Encryption Computer Engineering Dep. Lecturer: Dr. Fatimah Al-Ubaidy Classical Cryptography Class: Third Stage Substitution Cipher Example:Let the key string be Hello World and we want to encrypt the message hide the gold . Solution: Our key table would look like this: There is an odd number of letters in the plaintext, a Z is added to the last letter and the message is split into pairs of two letters. plaintext:HI DE TH EG OL DZ ciphertext: LF GD MW DN WO CV Security of Playfair: It is a great advance over simple monoalphabetic (i.e. caeser) ciphers. Whereas there are only 26 letters, there are 26 26 = 676 digrams (pairs of letters), so that identification of individual digrams is more difficult. 4






















