Data Security and User Authentication in Computer Engineering - Mustansiriyah University
Explore data security and user authentication concepts in Computer Engineering at Mustansiriyah University. Topics include asymmetric encryption, mutual authentication, one-way authentication, and federated identity management. Learn about protocols, encryption methods, and the importance of identity management systems in ensuring secure network access.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
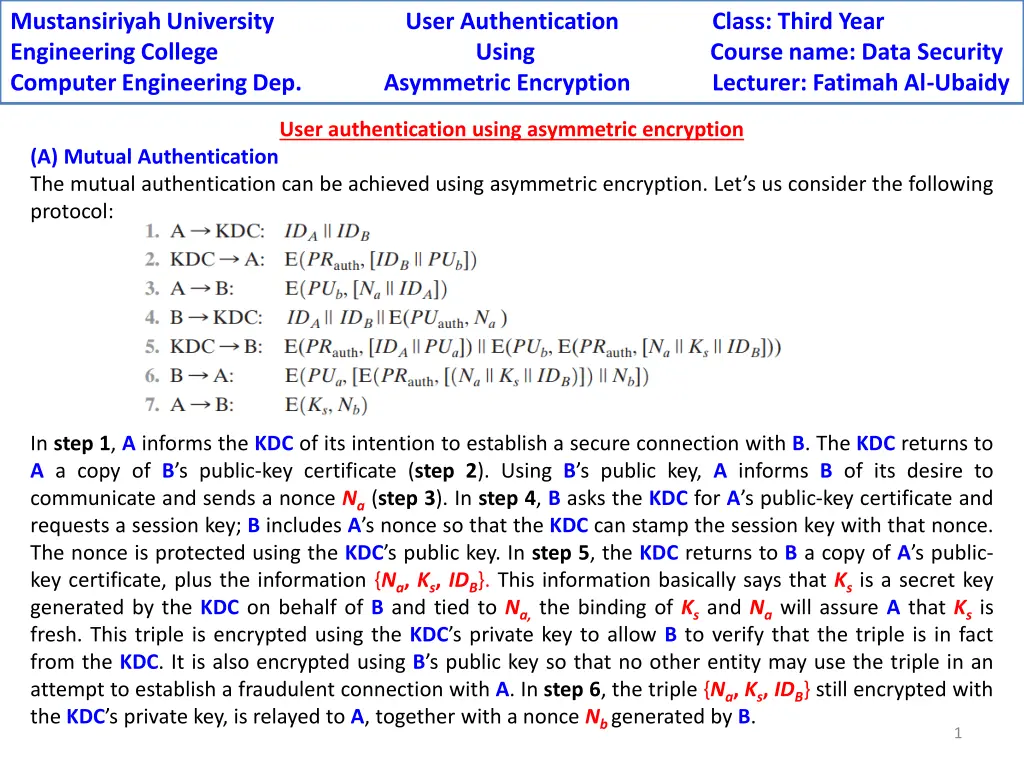
Mustansiriyah University Engineering College Using Course name: Data Security Computer Engineering Dep. Asymmetric Encryption Lecturer: Fatimah Al-Ubaidy User Authentication Class: Third Year User authentication using asymmetric encryption (A) Mutual Authentication The mutual authentication can be achieved using asymmetric encryption. Let s us consider the following protocol: In step 1, A informs the KDC of its intention to establish a secure connection with B. The KDC returns to A a copy of B s public-key certificate (step 2). Using B s public key, A informs B of its desire to communicate and sends a nonce Na (step 3). In step 4, B asks the KDC for A s public-key certificate and requests a session key; B includes A s nonce so that the KDC can stamp the session key with that nonce. The nonce is protected using the KDC s public key. In step 5, the KDC returns to B a copy of A s public- key certificate, plus the information {Na, Ks, IDB}. This information basically says that Ksis a secret key generated by the KDC on behalf of B and tied to Na, the binding of Ksand Na will assure A that Ksis fresh. This triple is encrypted using the KDC s private key to allow B to verify that the triple is in fact from the KDC. It is also encrypted using B s public key so that no other entity may use the triple in an attempt to establish a fraudulent connection with A. In step 6, the triple {Na, Ks, IDB} still encrypted with the KDC s private key, is relayed to A, together with a nonce Nb generated by B. 1
Mustansiriyah University Engineering College Using Course name: Data Security Computer Engineering Dep. Asymmetric Encryption Lecturer: Fatimah Al-Ubaidy User Authentication Class: Third Year All the foregoing are encrypted using A s public key. A retrieves the session key Ks uses it to encrypt Nb and returns it to B. This last message assures B of A s knowledge of the session key. (B) One-Way Authentication The public-key encryption approaches are suited to electronic mail, including the straightforward encryption of the entire message for confidentiality, authentication, or both. These approaches require that either the sender know the recipient s public key (confidentiality), the recipient know the sender s public key (authentication), or both (confidentiality plus authentication). If confidentiality is the primary concern, then the following may be more efficient: In this case, the message is encrypted with a one-time secret key. A also encrypts this one-time key with B s public key. Only B will be able to use the corresponding private key to recover the one-time key and then use that key to decrypt the message. This scheme is more efficient than simply encrypting the entire message with B s public key. If authentication is the primary concern, then a digital signature may suffice: This method guarantees that A cannot later deny having sent the message. 2
Mustansiriyah University Engineering College Using Course name: Data Security Computer Engineering Dep. Asymmetric Encryption Lecturer: Fatimah Al-Ubaidy User Authentication Class: Third Year Federated identity management Federated identity management (FIM) is an arrangement that can be made between multiple enterprises to let subscribers use the same identification data to obtain access to the networks of all the enterprises in the group. The use of such a system is sometimes called identity federation. Identity management is a centralized, automated approach to provide enterprise wide access to resources by employees and other authorized individuals. The focus of identity management is defining an identity for each user (human or process), associating attributes with the identity, and enforcing a means by which a user can verify identity. The central concept of an identity management system is the use of single sign-on (SSO). SSO enables a user to access all network resources after a single authentication. Identity federation is, in essence, an extension of identity management to multiple security domains. Such domains include autonomous internal business units, external business partners, and other third- party applications and services. The goal is to provide the sharing of digital identities so that a user can be authenticated a single time and then access applications and resources across multiple domains. Because these domains are relatively autonomous or independent, no centralized control is possible. Rather, the cooperating organizations must form a federation based on agreed standards and mutual levels of trust to securely share digital identities. 3
Mustansiriyah University Engineering College Using Course name: Data Security Computer Engineering Dep. Asymmetric Encryption Lecturer: Fatimah Al-Ubaidy User Authentication Class: Third Year SIM Standards In order for FIM to be effective, the partners must have a sense of mutual trust. Authorization messages between partners in an FIM system can be transmitted using Security Assertion Markup Language (SAML) or a similar XML standard that enables a user to log on once for affiliated but separate websites or networks. How federated identity management works (1) Users log in to their home network, authenticating through the home security domain. (2) After they have authenticated to the home domain, users initiate an attempt to log in to a remote application that uses identity federation. (3) Instead of authenticating directly with the remote application, that application requests the user's authentication from their home authentication server. (4) The user's home authentication server authorizes the user to the remote application and the user is permitted to access the application. Differences between FIM and SSO * Organizations that implement SSO do not necessarily use FIM. Identity federation, however, relies heavily on SSO technologies to authenticate users across domains. * While SSO lets a single authentication credential access different systems within one enterprise, an FIM system offers single-step access to numerous systems across different organizations. 4






















