Digital Signature Algorithm (DSA) in Data Security and Computer Engineering
Explore the implementation of the Digital Signature Algorithm (DSA) in the context of data security and computer engineering at Mustansiriyah University. Learn about the NIST approach, FIPS standards, sender-receiver interactions, verification processes, and example scenarios. Understand the importance of secure hash algorithms, private and public keys, and the role of random number generation in ensuring signature validity.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
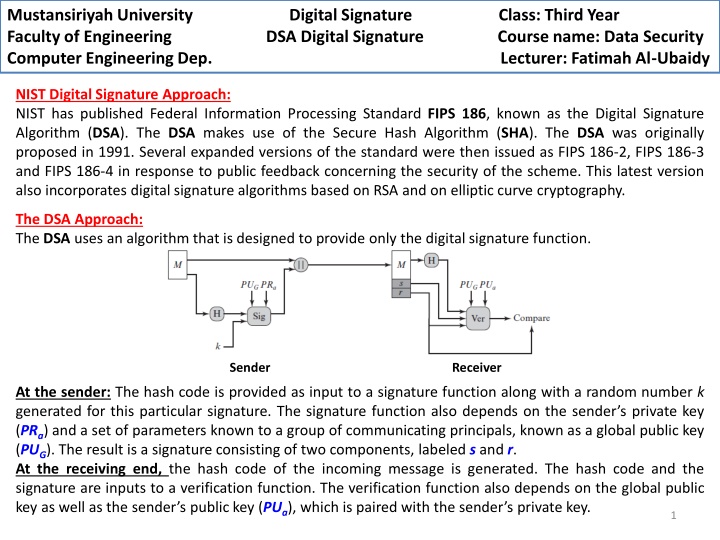
Mustansiriyah University Faculty of Engineering DSA Digital Signature Course name: Data Security Computer Engineering Dep. Lecturer: Fatimah Al-Ubaidy Digital Signature Class: Third Year NIST Digital Signature Approach: NIST has published Federal Information Processing Standard FIPS186, known as the Digital Signature Algorithm (DSA). The DSA makes use of the Secure Hash Algorithm (SHA). The DSA was originally proposed in 1991. Several expanded versions of the standard were then issued as FIPS 186-2, FIPS 186-3 and FIPS 186-4 in response to public feedback concerning the security of the scheme. This latest version also incorporates digital signature algorithms based on RSA and on elliptic curve cryptography. The DSA Approach: The DSA uses an algorithm that is designed to provide only the digital signature function. Sender Receiver At the sender: The hash code is provided as input to a signature function along with a random number k generated for this particular signature. The signature function also depends on the sender s private key (PRa) and a set of parameters known to a group of communicating principals, known as a global public key (PUG). The result is a signature consisting of two components, labeled sand r. At the receiving end, the hash code of the incoming message is generated. The hash code and the signature are inputs to a verification function. The verification function also depends on the global public key as well as the sender s public key (PUa), which is paired with the sender s private key. 1
Mustansiriyah University Faculty of Engineering DSA Digital Signature Course name: Data Security Computer Engineering Dep. Lecturer: Fatimah Al-Ubaidy Digital Signature Class: Third Year The output of the verification function is a value that is equal to the signature component rif the signature is valid. The signature function is such that only the sender, with knowledge of the private key, could have produced the valid signature. 2
Mustansiriyah University Faculty of Engineering DSA Digital Signature Course name: Data Security Computer Engineering Dep. Lecturer: Fatimah Al-Ubaidy Digital Signature Class: Third Year The signature of a message M consists of the pair of numbers rand s, which are functions of the public key components (p, q, g), the user s private key (x), the hash code of the message H(M), and an additional integer k that should be generated randomly or pseudorandomly and be unique for each signing. Let M, r , and s be the received versions of M, r, and s, respectively. Verification is performed using the formulas shown previously. The receiver generates a quantity vthat is a function of the public key components, the sender s public key, the hash code of the incoming message, and the received versions of r and s. If this quantity matches the r component of the signature, then the signature is validated. 3
Mustansiriyah University Faculty of Engineering DSA Digital Signature Course name: Data Security Computer Engineering Dep. Lecturer: Fatimah Al-Ubaidy Digital Signature Class: Third Year Example (2): Bob wants to send a message M to Alice which is to be signed with the DSA algorithm. Suppose the hash value of M is h(M) = 123, p = 1279, q=71, g=1157, k=10, x= 15. Then the signature and verification process is as follows: where y= 115715 mod 1279 = 851 4








