Enhancing Cyber Security for IEC 61850-Based Transmission Line Protection
Learn how Dr. Alexander Apostolov from OMICRON Electronics, USA, focuses on improving the cyber security of IEC 61850-based transmission line protection systems by detecting abnormal behaviors, defining prevention methods, and safeguarding against various threats including human errors and malicious attacks.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
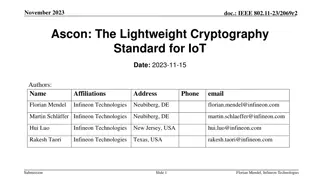
Improving the cyber security of IEC 61850 based transmission line protection Dr. Alexander Apostolov OMICRON electronics, USA C1 - Internal
Introduction C1 - Internal
Questions? What are we doing? Why are we doing it? How are we doing it? C1 - Internal
What are we doing? Detecting abnormal behavior of the electric power system and its protection, automation and control systems Defining methods and tools to identify the reasons for the abnormal behavior Defining methods and tools to prevent or reduce the impact of abnormal behavior caused by humans C1 - Internal
Why are we doing it? To protect the electric power grid and its equipment from short term or long-term damage caused by: Natural weather or other random events Human errors during maintenance or system operation Intentional actions by disgruntled employees Random attacks by unsophisticated hackers Malicious attacks by highly skilled hackers C1 - Internal
How are we doing it? Based on: Understanding of the threats operation of primary equipment, change of the configuration of an IED, publishing of IEC 61850 messages, etc. Understanding of the impact of specific threats Knowledge of the electric power system parameters and connectivity (digital twin) C1 - Internal
How are we doing it? Knowledge of the electric power system real time topology Knowledge of the communications architecture Knowledge of the communications system configuration Knowledge of the capabilities of the components of the SPACS (digital twins) Knowledge of the configuration of the IEDs C1 - Internal
How are we doing it? Knowledge of the IEC 61850 standard Knowledge of the level of implementation of IEC 61850 in the IEDs Knowledge of the test system Continuous collection and analysis of data available from various sources IEDs, MUs, PMUs, weather information, scheduled events information, etc C1 - Internal
How are we doing it? Analysis of the data using different methods expert systems, AI tools, comparison between predicted behavior and actual behavior, etc. C1 - Internal
IEC 61850 C1 - Internal
IEC 61850 Services Page 11 C1 - Internal
Control Blocks Server IEC 61850 Services BUFFERED- REPORT- CTRL-BLOCK 1 0..* 0..* 1..* UNBUFFERED- REPORT- CTRL-BLOCK Logical Device 0..* 0..* 1 1 0..* LOG- CONTROL- BLOCK 0..* 0..* 1..* LOG Logical Node 1 0..1 1 1 1 1 1 SETTING- GROUP- CONTROL-Block LLN0 0..* 1 0..1 1 GOOSE- CONTROL-BLOCK 0..* 1 0..1 GSSE- CONTROL-BLOCK 1 0..1 1 MULTICAST- SAMPLED- VALUE-CTRL-B. 0..1 0..* 1 0..* UNICAST- SAMPLED VALUE-CTRL-B. 1 0..1 1 1..* 1 1 1 1 1 1 1 0..* 0..* DATA DATA DataSet 1 1 1..* Substitution Substitution Time Time DataAttribute 0..* Control File File Page 12 C1 - Internal
GOOSE message C1 - Internal
Sampled Values Communications 7/1/2025 14 C1 - Internal
Accelerated transmission line protection C1 - Internal
IEC 61850 Based Accelerated Line Protection A F3 F1 F2 B A Distance Protection 1 B Distance Protection 1 A Distance Protection 2 B Distance Protection 2 t C1 - Internal
IEC 61850 Based Accelerated Line Protection F3 F1 F2 A B A Distance Protection 1 B Distance Protection 1 MPLS R-GOOSE A Distance Protection 2 B Distance Protection 2 C1 - Internal
Security issues C1 - Internal
Security Issues Transition from local to some forms of distributed protection functionality Requirements for more efficient communications based protection schemes Need for local and remote user interface from different types of corporate clients Page 19 C1 - Internal
Security Issues Use of protection IEDs as the main data source for integrated data acquisition and control systems Use of multifunctional IEDs as distributed power system disturbance recording devices It is not an IEC 61850 problem Page 20 C1 - Internal
Threats Sources Natural disasters and equipment failure Well-intentioned employees who make inadvertent errors, use poor judgment, or are inadequately trained Employees with criminal intent to profit or to damage others by the misappropriation of utility resources Disgruntled employees or ex-employees who cause damage to satisfy a grudge C1 - Internal
Threats Sources Hobbyist intruders who gain pleasure from unauthorized access to utility information systems Criminal activity by both individuals and organizations directed against the utility, its employees, customers, suppliers, or others Terrorists C1 - Internal
Threats Sources Competing organizations searching for proprietary information of the utility, its suppliers, or customers Unscrupulous participants in the markets for electric power or derivatives Software providers who, in attempting to protect their intellectual property rights, create vulnerabilities or threaten to disable the software in contractual disputes C1 - Internal
Hacked GOOSE Messages: Page 24 C1 - Internal
Hacked Sampled Values Communications 7/1/2025 25 C1 - Internal
Mitigation C1 - Internal
GOOSE in WireShark C1 - Internal
IEC 61850 90-5 Session Protocol Session Identifier (SI) = 0xA0 (8 bit) - Tunnelled 0xA1 (8 bit) - GOOSE 0xA2 (8 bit) Sample value 0xA3 (8 bit) Management Session Identifier (SI) Session Header Length (LI) (8 bit) Session Header Header Content Indicator(PI) = 0x80 (8 bit) Session Header Length LI (8 bit) SPDU Length (32 bits) Security Information SPDU Number (32 bits) Version = 2 (8 bit) LI Time of Current Key (32 bits)) Signature domain Time of Next Key (16 bits) Key ID (32 bits) Session User Information Initialization Vector (IV 1-233 bytes) SPDU Length PayloadLength (32 bit) 1..n PDUs Payload Length Length Payload GOOSE APDU Encrypted domain Simulation Padding (0xAF) Choice of APPID PaddingLength (8 bits) m PaddingLength =m APDU Length SV APDU Padding (m bytes) goosePdu Simulation Signature (size of signature +2 bytes) APPID APDU Length SavPdu MNGT APDU Tunnelled Simulation Simulation APPID APPID APDU Length Dst MAC VLAN mngtPdu IEEE 802.1p Frame Length GOOSE or SV Ethertype packets + Ethernet Pad Bytes C1 - Internal
Functional security Based on the protection scheme principle (POTT) Based on redundant data (DTT) C1 - Internal
Functional security testing The implementation of the functional security capability requires proper testing to verify that it is operating as expected under different electric power system conditions. The test system needs to be capable of simulating normal power flow, as well as short circuit fault conditions to verify that the transmission line protection scheme will operate when a short circuit fault occurs without the additional time delay based on the received GOOSE message from the remote end of the line. C1 - Internal
Conclusions The availability of specific features in the GOOSE publishing mechanisms allows for the development of intrusion detection methods that can be implemented in the subscribing IEDs. The intrusion detection is based on the monitoring of state and sequence numbers, as well as data attribute value changes. Additional end-to-end security is implemented in R- GOOSE based on IEC 62351-6. Using good understanding of the protection system of the transmission line and its operation during different fault conditions can be used to implement a mechanism of functional security that will prevent the undesired tripping of the transmission line even if an intruder has been able to successfully avoid the cyber security protection mechanisms. C1 - Internal
Thank you Dr. Alexander Apostolov alex.apostolov@omicronenergy.com +13103514574 C1 - Internal