FTM Protection Mechanism for IEEE 802.11-17
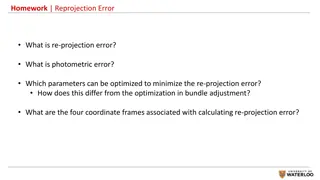
Explore the May 2017 discussion on FTM protection and the mechanism for successful rage estimation attacks in IEEE 802.11-17. Learn about VHT-LTF usage, ToA estimation, and the implications for security aspects against Type B adversaries.
Uploaded on | 1 Views
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
May 2017 Discussion on FTM Protection follow up doc.: IEEE 802.11-17/0801r1 Date: 2017-05-09 Authors: Name Benny Abramovsky Chittabrata Ghosh Affiliations Intel Address Phone email Benny.Abramovsky@intel.com Jonathan Segev Qinghua Li Nehru Bhandaru Broadcom Submission Slide 1 Abramovsky, Ghosh, Segev & Li, Intel
May 2017 doc.: IEEE 802.11-17/0801r1 Abstract This submission is a follow-up from previous telecon on security aspects for Type B adversary Submission Slide 2 Abramovsky, Ghosh, Segev & Li, Intel
May 2017 Mechanism for successful rage estimation attack doc.: IEEE 802.11-17/0801r1 VHT-LTF usage: Decoding vs. ToA Decoding uses the dominant path where most of the energy is concentrated to maximize likelihood of successful decoding. The 1st tap is used to identify the first path rather then dominant path. Affecting ToA estimation only By transmitting a spoofed time advanced VHT- LTF with minimal power the ToA estimation is greatly affected with minimal impact on decoding probability. Source: https://www.researchgate.net/publication/273443111 Submission Slide 3 Abramovsky, Ghosh, Segev & Li, Intel
May 2017 doc.: IEEE 802.11-17/0801r1 Q: Is this attack simple to generate? A: Yes, hacker can configure NIC to transmit NDP frame in response to FTM frame at low power. ISTA Transmission VHT- STF VHT- SIG-B L-STF L-LTF L-SIG VHT-SIG-A VHT-LTF Data VHT SIG - B VHT - STF L-STF L-LTF VHT-SIG-A VHT-LTF L-SIG Dozens of Nano-second shifting F.E shifting 67ns 10m shift Adversary NDP ToF Measurement RSTA Spoofed ISA Range ISTA actual position Type B Adversary Allowed Area Submission Slide 4 Abramovsky, Ghosh, Segev & Li, Intel
May 2017 doc.: IEEE 802.11-17/0801r1 Q: What about timing? A: It is a bad practice to rely on PHY properties as a protection mechanism. The adversary may move around freely between the RSTA and the ISTA until the desired attack timing is obtained and the attack is successful. ToF Measurement RSTA Spoofed ISA Range ISTA actual position Adversary moves around Allowed Area Submission Slide 5 Abramovsky, Ghosh, Segev & Li, Intel
May 2017 doc.: IEEE 802.11-17/0801r1 Q: Wouldn t it create ACK decode error on RSTA side? A: No, the spoofed signal is perceived as multipath somewhat hindering the SINR while still allow for correct decoding while giving a wrong sense of distance. Submission Slide 6 Abramovsky, Ghosh, Segev & Li, Intel
May 2017 doc.: IEEE 802.11-17/0801r1 Summary REVmc FTM uses ACK frames for measurements purposes only. The ACK doesn t contain any information unknown to the attacker. This submission demonstrates a measurement attack over the ACK, with no specialized HW and no impact on successful ACK decoding. Thus, it is not useful to protect the ACK at the MAC level from these types of attack. Submission Slide 7 Abramovsky, Ghosh, Segev & Li, Intel
May 2017 doc.: IEEE 802.11-17/0801r1 Straw poll 1 Do you agree that for REVmc, HEz, and VHTz FTM modes the fields over which range measurements is performed shall be protected for spoofing prevention against a Type B adversary? Yes: 14 No: 0 Abstain: 2 Submission Slide 8 Abramovsky, Ghosh, Segev & Li, Intel
May 2017 doc.: IEEE 802.11-17/0801r1 Motion Move to adopt the following text to the SFD and instruct the SFD editor to include it in TGaz SFD under the security section and grant editorial license to SFD Editor For REVmc, HEz, and VHTz FTM modes the fields over which range measurements are performed shall be protected against a Type B adversary attack Moved by: Nehru Bhandaru Seconded: SK Yong Yes: 17 No: 0 Abstain: 1 Motion passes Submission Slide 9 Abramovsky, Ghosh, Segev & Li, Intel