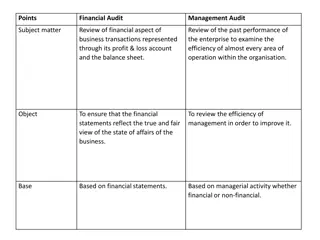
Government Audit Status Update
Action plan progress update, current audit status, and utilization of performance measures in a government setting. Includes details on tasks, issues resolution steps, and major outstanding reconciliations. Learn how federal qualifications are assessed and key focus areas for audit completion.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
60 min OSTMM THE OPEN SOURCE SECURITY TESTING METHODOLOGY MANUAL DAY 02
AGENDA WHAT YOU NEED TO KNOW SECURITY ANALYSIS OPERATIONAL SECURITY METRICS TRUST ANALYSIS THE WORKFLOW 2
What you need to know ALL ABOUT OPSEC MOVE ASSET AS FAR FROM THREAT AS POSSIBLE NEUTRALISE THREAT (BY INPUT SANITISATION I.E.) DESTROY THE THREAT 100% SECURITY IS POSSIBLE IF WE CAN COVER THAT THE THREAD AND ASSET ARE SEPERATED IN PRACTICE, NEARLY IMPOSSIBLE. 4
What you need to know CONTACT BETWEEN ASSET AND OUTSIDE WORLD SOMETIMES REQUIRED EVERY ENTRY ENTRY POINT INCREASES POROSITY MORE POROSITY = LESS SECURITY A PORE CAN BE VISIBILITY , ACCESS OR TRUST THE ASSETS CAN BE ACCESS THROUGH PORES WITH VARIOUS CONTROLS 5
12 10 CONTROLS WE LOST 2 ALONG THE WAY
12 12 10 CONTROLS - INTERACTIVE AUTHENTICATION INDEMNIFICATION A CONTRACT ENFORCEDBETWEEN ASSETANDTHEINTERACTING PARTIES RESILIENCE SUBJUGATION ASSURESINTERACTIONSCAN ONLYOCCURACCORDING TODEFINEDPROCESS CONTINUITY 7
12 12 10 CONTROLS - INTERACTIVE AUTHENTICATION INDEMNIFICATION A CONTRACT ENFORCEDBETWEEN ASSETANDTHEINTERACTING PARTIES RESILIENCE SUBJUGATION ASSURESINTERACTIONSCAN ONLYOCCURACCORDING TODEFINEDPROCESS CONTINUITY 8
OBJECTIVES VS CONTROLS WHAT TO DO WHEN AND WHY
LIMITATION LET S ADD ANOTHER LAYER
limitations 12
THE METHODOLOGY BRINGING IT ALL TOGETHER
THE METHODOLOGY FOREVERYCONTACT POINTOFASSETWITH OUTSIDEACTOR ? FOREVERYHOLE ? APPLYAT MAX.10CONTROLS ? TOCOVER4LIMITATIONS ? ANDBRING SECURITYBACK UPTO100% APPLIESTOA SNAPSHOTANDNEEDSTOBE RE-EVALUATED REGULARLY 14
WHAT YOU HAVE TO DO COVERING THE COVERAGE
DEFINE A SECURITY TEst 7 STEPS FOR EVERY SECURITY TEST ? DEFINEYOURASSETS,CONTROLS AND LIMITATIONS ? DEFINEAREAS AROUND THE ASSET,THISISTHE ENGAGEMENTZONE ? DEFINEEVERYTHINGAROUND ENGAGEMENTZONE,THISISSCOPE ? DEFINETHE INTERACTIONOF THESCOPEWITHTHE WORLD, THISIS THE VECTORS ? DEFINEEQUIPMENTREQUIRED,THESEARE THE CHANNELS ? DEFINETESTTYPE ? DEFINERULES OF ENGAGEMENT 16
scope TOTAL POSSIBLE OPERATING SECURITY ENVIRONMENT ? FORANY INTERACTIONWITH ANY ASSET ? MAYINCLUDE THE PHYSICALCOMPONENTSOFSECURITYMEASURESAS WELL. 17
CHANNELS 18
4 POINT PROCESS INDUCTION(Z) ? UNDERSTANDINGWHERE THE TARGETRESIDESANDFROMWHERE. INQUEST(C) INTERACTION(A/B <>B/A) INTERVENTION(X/Y/Z) 19
TRIFECTA HOWDOCURRENT OPERATIONSWORK? HOWDOTHEYWORK DIFFERENTLYFROMHOWMANAGEMENTTHINKSTHEYWORK? HOWDOTHEYNEEDTOWORK? 20
Test results 1.DATEAND TIMEOFTEST 2.DURATIONOFTEST 3.NAMES OFRESPONSIBLEANALYSTS 4.TESTTYPE 5.SCOPEOFTEST 6.INDEX (METHODOFTARGETENUMERATION) 7.CHANNEL TESTED 8.TESTVECTOR 9.ATTACKSURFACEMETRIC 10.WHICHTESTSHAVEBEENCOMPLETED,NOTCOMPLETED,ORPARTIALLY COMPLETED,AND TOWHATEXTENT 11.ANY ISSUESREGARDINGTHETESTAND THEVALIDITY OFTHERESULTS 12.ANY PROCESSESWHICHINFLUENCETHESECURITYLIMITATIONS 22 13.ANY UNKNOWNS ORANOMALIES
FALLACIES OF TESTING NOTHING IS EVER 100% SECURE ? THIS FAILS TO TAKE TIME AND CONDITIONS INTO REGARD EVEN IF YOU ARE SECURE, IF AN ATTACKER WANTS IN BADLY ENOUGH THEY LL GET IN. ? THIS IMPLIES ATTACKERS DID NOT WANT IT BADLY ENOUGH BESIDES, GET IN IS A VERY BROAD UNDERSTANDING THERE IS NO PERFECT SECURITY. ? THERE CAN BE PERFECT SECURITY FOR THE REQUIREMENTS AS COVERED BY TESTS SECURITY IS A PROCESS NOT A PRODUCT. ? IT CAN BE BOTH AND MORE! 23
METRICS RAV CALC ? POROSITY ? + CONTROLS ? + LIMITATIONS ? ACTUAL SECURITY % ON ITERATIONS, THIS NEEDS TO RISE SEE EXCEL FILE 006 RAV CALC.XLSX 24