Introduction to Modern Cryptography in Education Systems
In the world of cryptography, the exploration of modern encryption techniques and their application in various educational institutions worldwide is a fascinating journey. Discover the impact of cryptography on daily life, the depth of its theoretical foundations, and the similarities among renowned universities that delve into this intriguing field. From understanding attackers' mindsets to replicating educational systems, the realm of cryptography offers a blend of complexity, importance, and fun.
Uploaded on Mar 16, 2025 | 2 Views
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
Cryptography Lecture 1
Welcome! Crypto is amazing Can do things that initially seem impossible Crypto is important It impacts each of us every day Crypto is fun! Deep theory Attackers mindset
Somewhat A replication of UMD Crypto Same education system as College Park Same textbook as College Park Introduction to Modern Cryptography (2nd edition) Jonathan Katz and Yehuda Lindell Almost same evaluation as College Park Aalto University (Finland) Bar-Ilan University (Israel) Ben-Gurion University (Israel) Boise State University Boston University Brown University Caltech City University of New York Colgate University Columbia University Cornell University Florida Institute of Technology Florida State University George Washington University Georgia Institute of Technology Harvard University IIIT Bangalore Indiana University Indian Institute of Science, Bangalore Johns Hopkins University Ko University Saarland University (Saarland, Germany) Saarland University (Saarland, Germany) La Sapienza (University of Rome, Italy) McGill University (Canada) McMaster University Miami University Northeastern University Northeastern University NYU Ohio State Paderborn University (Germany) Pennsylvania State University Princeton University Purdue University Purdue University Ruhr-University Bochum (Germany) Simon Fraser University (Canada) Stanford University Technologies Net Alliance (Pakistan) Tel-Aviv University (Israel) Tsinghua Univeristy (China) TU Eindhoven Tufts University Universidade Federal de Pernambuco (Brazil) Universitadi Salerno (Italy) UniversiteCatholique de Louvain (Belgium) (see also here) University College, London (UK) University of Amsterdam University of Beira Interior University of Bologna (Italy) University of Bonn University of Brasilia University of Bucharest, Romania University of California, Berkeley University of California, Davis University of California, Irvine University of Calgary (Canada) University of Chicago University of Colorado, Denver University of Genoa University of Haifa UIUC University of Maryland University of Michigan University of Nebraska-Lincoln University of North Florida University of Oldenburg (Germany) University of Pennsylvania University of Pittsburgh USC UT Austin University of Virginia Wellesley College
With Significant Modifications Cross-listed course UMBC does not have an advanced crypto class Teaching what s most essential Focusing on practical things Including some advanced topics (not much) Adding blockchains Removing the underlying design of blockcipher design Removing stream cipher design At a slightly slower pace Our semester is shorter than that of College Park
Necessary administrative stuff Course webpage https://www.csee.umbc.edu/~hbzhang/teaching. html Or Google Haibin Zhang + UMBC Prerequisites/information posted there Syllabus posted there HWs posted there Announcements posted there
Necessary administrative stuff Historically, 10-15% of the class drops by end of first full week More may drop after a while (or not) If you are trying to get in, do the first HW even if not yet admitted If you do not do the first HW and enroll late, you do not get credit.
TA Chao Liu Half-time TA chaoliu717@umbc.edu
This is a tough class Mathematical prerequisites Discrete math, probability, modular arithmetic Requires mathematical maturity Proofs, abstraction
This is a tough class CS prerequisites Binary, hex, pseudocode/algorithms, big-O notation (Theory of computation/computational complexity/Reduction) Programming assignments Hard part should not be the programming, but the thought behind it Flexibility in choice of language
Active Learning Try to promote active learning MUST read textbook before class Lecture will move quickly, expect questions and discussion Quiz (if not every week)!!
Textbook Required textbook: Introduction to Modern Cryptography, 2ndedition, Katz and Lindell Exams will be open book Physical copies only
HWs/exams 3-4 HWs Mostly theory Some implementation No late HWs; I will give you enough time; do not start doing them just before the deadline. In-class midterm and final Questions similar to optional HWs and in-class exercises; may also be based on assignments Anything covered in class or listed on syllabus, or what I ask you to read in the book is fair game
Need to Attend Every Lecture Sign up if there is no quiz TA handles it If you are sick or have an excused leave, you need to prove it to the TA and me.
Evaluation Attendance and participation 5% Quiz: 20% HWs: 15% Midterm: 30% Final: 30%
How to reach me Best way to contact me is by email: hbzhang@umbc.edu Please put CMSC-443/652d in subject line Office hours after class 11:15-12pm TuTh; priority given to students who need to rush to other classes TA office hour To be determined
Questions? Please ask questions throughout!
Course goals Understand real-world crypto via a rigorous approach When you encounter crypto in your career: Understand the key terms Understand the security guarantees provided Know how to use crypto Understand what goes on under the hood Proofs! Reduction!
Course non-goals Designing your own crypto schemes Implementing your own crypto for real-world use
Cryptography (historically) the art of writing or solving codes Historically, cryptography focused exclusively on ensuring private communication between two parties sharing secret information in advance (using codes aka private-key encryption)
Modern cryptography Much broader scope! Data integrity, authentication, protocols, The public-key setting Group communication More-complicated trust models Foundations (e.g., number theory, quantum- resistance) to systems (e.g., electronic voting, cryptocurrencies)
Modern cryptography Design, analysis, and implementation of mathematical techniques for securing information, systems, and distributed computations against adversarial attack
Modern cryptography Cryptography is ubiquitous Passwords, password hashing Secure credit-card transactions over the internet Encrypted WiFi Disk encryption Digitally signed software updates Bitcoin
Cryptography (historically) the art of writing or solving codes Historically, cryptography was an art Heuristic, unprincipled design and analysis Schemes proposed, broken, repeat
Modern cryptography Cryptography is now much more of a science Rigorous analysis, firm foundations, deeper understanding, rich theory The crypto mindset has permeated other areas of computer security Threat modeling Proofs of security
Rough course outline Secrecy Integrity Private-key setting Private-key encryption Message authentication codes Public-key setting Public-key encryption Digital signatures Building blocks Pseudorandom (number) generators Pseudorandom functions/block ciphers Hash functions Number theory
Motivation Allows us to ease into things , introduce notation Shows why unprincipled approaches are dangerous Illustrates why things are more difficult than they may appear
Classical cryptography Until the 1970s, exclusively concerned with ensuring secrecy of communication I.e., encryption
Classical cryptography Until the 1970s, relied exclusively on secret information (a key) shared in advance between the communicating parties Private-key cryptography aka secret-key / shared-key / symmetric-key cryptography
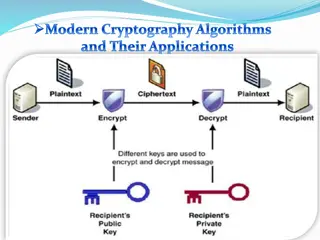
Private-key encryption key key ciphertext c k k m m := Deck(c) c := Enck(m) message/plaintext decryption encryption
Private-key encryption k c m c := Enck(m) c c k m := Deck(c)
Private-key encryption A private-key encryption scheme is defined by a message space M M and algorithms (Gen, Enc, Dec): Gen (key-generation algorithm): outputs k K K Enc (encryption algorithm): takes key k and message m M M as input; outputs ciphertext c c Enck(m) Dec (decryption algorithm): takes key k and ciphertext c as input; outputs m or error m := Deck(c) For all m M M and k output by Gen, Deck(Enck(m)) = m
Kerckhoffss principle The encryption scheme is not secret The attacker knows the encryption scheme The only secret is the key The key must be chosen at random; kept secret Some arguments in favor of this principle Easier to keep key secret than algorithm Easier to change key than to change algorithm Standardization Ease of deployment Public validation
The shift cipher Consider encrypting English text Associate a with 0; b with 1; ; z with 25 k K K = {0, , 25} To encrypt using key k, shift every letter of the plaintext by k positions (with wraparound) Decryption just does the reverse helloworldz ccccccccccc jgnnqyqtnfb
Modular arithmetic x = y mod N if and only if N divides x-y [x mod N] = the remainder when x is divided by N I.e., the unique value y {0, , N-1} such that x = y mod N 25 = 35 mod 10 25 [35 mod 10] 5 = [35 mod 10]
The shift cipher, formally M M = {strings over lowercase English alphabet} Gen: choose uniform k {0, , 25} Enck(m1 mt): output c1 ct, where ci := [mi + k mod 26] Deck(c1 ct): output m1 mt, where mi := [ci - k mod 26] Can verify that correctness holds
Is the shift cipher secure? No -- only 26 possible keys! Given a ciphertext, try decrypting with every possible key Only one possibility will make sense (What assumptions are we making here?) Example of a brute-force or exhaustive- search attack
Example Ciphertext uryybjbeyq Try every possible key tqxxaiadxp spwwzhzcwo helloworld