RBSSO Protocol: Sequence
RBSSO Protocol describes the sequence of steps involved in initializing a session between a client and a cloud service in a secure manner. It involves processes such as obtaining service tokens, authentication, session key exchange, and request handling. The protocol ensures secure communication and data exchange between the client and the cloud service provider.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
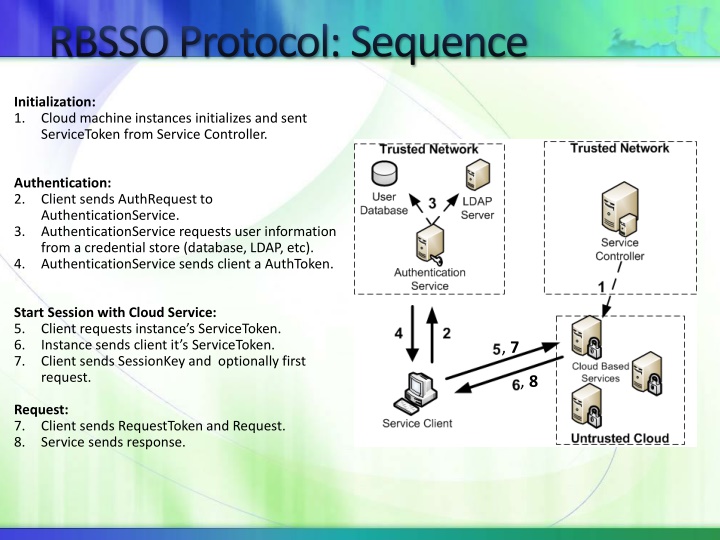
RBSSO Protocol: Sequence Initialization: 1. Cloud machine instances initializes and sent ServiceToken from Service Controller. Authentication: 2. Client sends AuthRequest to AuthenticationService. 3. AuthenticationService requests user information from a credential store (database, LDAP, etc). 4. AuthenticationService sends client a AuthToken. Start Session with Cloud Service: 5. Client requests instance s ServiceToken. 6. Instance sends client it s ServiceToken. 7. Client sends SessionKey and optionally first request. , 7 , 8 Request: 7. Client sends RequestToken and Request. 8. Service sends response.
RBSSO Protocol: ServiceToken ServiceToken Byte +0 +1 +2 +3 +4 +5 +6 +7 Header (5 bytes) Version Message Length 1..5 Time Stamp 6 .. 13 Service List Length (sl) 14 .. 17 Service List 18.. sl+17 Body SKpub Length (skp) sl+18 .. sl+21 sl+22 .. sl+21+skp ANS.1 Encoded SKpub sl+22+skp .. sl+25+skp Text Length (tx) String(Public IP or Host + Delimiter + Instance ID + Delimiter + Service Controller ID + Delimiter + Service ID) sl+26+skp .. sl+25+skp+tx Message Signature Signature(SCpri, Version + Body) sl+26+skp+tx .. end of token Tail
RBSSO Protocol: AuthRequest AuthRequest Byte +0 +1 +2 +3 +4 +5 +6 +7 +8 Header (9 bytes) Version Message Length Body Length 1..9 Time Stamp 1..8 Request ID 9..16 CKpub Length (ckp) 17..20 ANS.1 Encoded CKpub 21 .. ckp+20 Body (Encrypted with CKsec) ckp+21 .. ckp+24 Text Length (tx) ckp+25 .. ckp+24+tx String(AuthServer ID + Delimiter + User ID + Delimiter + Role ID) ckp+25+tx .. end of body User Credentials CKsec Length (cks) 1 .. 4 ANS.1 Encoded CKsec Tail 5 .. cks + 4 (Encrypted with AKencpub) Message Hash cks + 5 .. end of tail Hash(Version + Body + CKsec Length + CKsec)
RBSSO Protocol: AuthToken AuthToken Byte +0 +1 +2 +3 +4 +5 +6 +7 Header (5 bytes) Version Message Length 1..5 Time Stamp 6..13 Expiry Date 14..21 Session ID 22.. 29 CKpub Length (ckp) Encrypted with CKsec 30..33 Body ANS.1 Encoded CKpub 34 .. ckp+33 ckp+34 .. ckp+37 Text Length (tx) ckp+38 .. ckp+37+tx String(AuthServer ID + Delimiter + User ID + Delimiter + Role ID) Message Signature Signature(AKsigpri, Version + Body) ckp+38+tx .. end of token Tail
RBSSO Protocol: SessionKey SessionKey Byte +0 +1 +2 +3 +4 +5 +6 +7 Header (5 bytes) Version Message Length 1..5 Encrypted with SKpub Random Number 6 .. 13 Body 14.. end of SessionKey ANS.1 Encoded SEKsec
RBSSO Protocol: RequestToken RequestToken Byte +0 +1 +2 +3 +4 +5 +6 +7 Header (5 bytes) Version Message Length 1..5 Time Stamp 6..13 Request ID 14..21 Session ID 22.. 29 Encrypted with SEKsec Body Request Hash Length (rh) 30..33 Request Hash 34 .. rh+33 rh+34 .. rh+37 Text Length (tx) rh+38 .. rh+37+tx String(Service ID) Message Signature Signature(CKpri, Version + Body) rh+38+tx .. end of token Tail
Performance Implementation of AuthSrever and Client created using Java TCP sockets. Authentication performance evaluated against a SSL connection and Kerberos. Performance measured in average time per request on low latency local network and higher latency, nosier wide area network. Each protocol was tested with 10,000 authentication requests for each network. Lakehead University's private cloud computing testbed
Authentication Performance Average Request Time Per Run LAN 70 60 50 Milliseconds 40 RBSSO SSL 30 Kerberos 20 10 0 1 2 3 4 5 6 7 8 9 10 Run Based on 1,000 requests per run per protocol.
Authentication Performance Average Request Time Per Run Internet 1000 900 800 700 600 Milliseconds RBSSO 500 SSL 400 Kerberos 300 200 100 0 1 2 3 4 5 6 7 8 9 10 Run Based on 1,000 requests per run per protocol.
Authentication Performance Average Request Time 900 800 700 600 Milliseconds 500 400 300 200 100 0 Internet LAN RBSSO 276.7162 36.8437 SSL 809.5823 59.7964 Kerberos 367.0858 29.0673 Based on 10,000 requests per protocol.
Future Work Expand on roll model. Performance testing of all parts of the protocol. Formal security evaluation of the protocol. Securing data on the cloud.