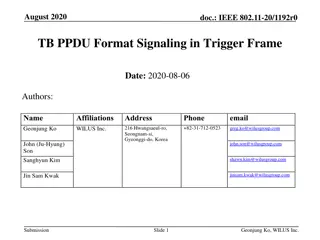
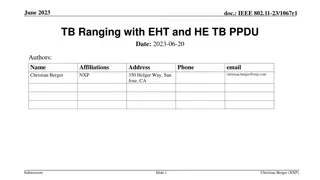
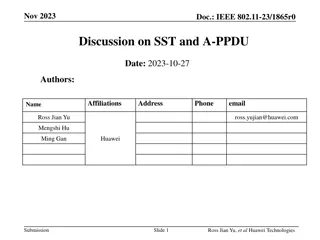
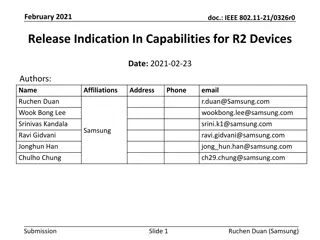
Reducing PAPR in EHT.ER.SU.PPDU for Enhanced Wi-Fi Transmission
To address PAPR issues in the EHT.ER.SU.PPDU for extended range Wi-Fi systems, this document explores methods to mitigate signal distortion and improve transmission performance. The frequency-duplicated data part causing PAPR increase is analyzed, highlighting the impact on both indoor and outdoor environments. Solutions are proposed to reduce PAPR for better hardware implementation and signal quality.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
Committing AE from Sponges: Security Analysis of the NIST LWC Finalists Juliane Kr mer, Patrick Struck, and Maximiliane Weish upl
Partitioning Oracle Attack [LGR21] ?0 ?1 ?2 ?3 ?4 ?5 ?6 ?7 ?8 ?9 Finds ?,?, and ? such that: Dec ?0,?,?,? Dec ?1,?,?,? Dec ?2,?,?,? Dec ?3,?,?,? Dec ?4,?,?,? Decryption error ? ?0 ?1 ?2 ?3 ?4 ?5 ?6 ?7 ?8 ?9 Dec ?5,?,?,? = Dec ?6,?,?,? = Dec ?7,?,?,? = Dec ?8,?,?,? = Dec ?9,?,?,? = Alice ?8 Bob ?8 Further attacks: Fast message franking [DGRW18] Subscribe with Google [ADG+22] ?1 ?2 3
Committing Security [FLPQ13] [ABN10] [FOR17] [CR22] [BH22] [MLGR23] More fine-grained notions Robustness for PKE Robustness for AE CMT Security for AE CMT-1, CMT-3 CMT-4 CMT-K CMT 4
NIST LWC Standardization Process March 2021 August 2018 April 2019 February 2023 August 2019 Call for lightweight cryptographic standards for AE 32 round-2 candidates 56 round-1 candidates 10 finalists Ascon wins! PHOTON-Beetle Xoodyak Ascon ISAP SCHWAEMM Elephant Romulus GIFT-COFB TinyJambu Grain-128AEAD Permutation-based Block-cipher-based Dedicated design 5
Overview Analysis Goal: analyze the committing security of the NIST LWC finalists Consider the schemes based on (tweakable) block-ciphers or permutations Focus on the main parameter set for each candidate Analyze the AE mode of the schemes, assume underlying primitives to be ideal 7
Overview Results a CMT attack with essentially no queries a CMT attack with significantly less than 264queries * * about 64-bit CMT security *[NSS23] and [DGL23] also give results on the committing security of Ascon and TinyJambu, respectively. 8
Our Proofs boil down to Modelling the schemes as plain sponges Extra care necessary for scheme- specific features Re-keying mechanism in ISAP State- / Output-blinding in Ascon State-Update-Function, Rate-Whitening, and Output-blinding in SCHWAEMM Bounding the probability of finding colliding tags 9
Our Attacks boil down to At some point in the scheme, the whole state is adversary-controlled. this is true for the initial state. the adversary-controlled state is large. The tag is too short. 10
Romulus Based on tweakable block-ciphers Follows the Context-pre- Processing (CpP) approach 11
Romulus: Committing Attack General attack strategy: Choose (?,?,?,?) and compute ?,? Invert ????on ?,? under ? and ? (? ,? ) Find ? s.t. ????(? ,? ,? ) = ? 12
Zero-Padding (ZP) [ADG+22] Simple, non-invasive method to obtain CMT-K security For Ascon: ZP can increase CMT security [NSS23] Can we achieve CMT-K security for the NIST LWC finalists using ZP? Can we use ZP to increase the CMT security of secure schemes in general? 15
Zero-Padding Results For full-CpP schemes, we show: Attacks against ZP-PHOTON-Beetle and ZP-Xoodyak not CMT-K secure if: number of zeros block size otherwise: security increases with number of padded zeros ZP-Elephant: ZP-ISAP: no increase in CMT security (unlike for Ascon) 16
Conclusion 6 committing attacks, 3 proofs Several negative results regarding Zero- Padding ePrint 2023/1525 maximiliane.weishaeupl@ur.de 17
References [ABN10] [ADG+22] Abdalla, Bellare, Neven. Robust Encryption. TCC 2010. Albertini, Duong, Gueron, K lbl, Luykx, and Schmieg. How to abuse and fix authenticated encryption without key commitment. USENIX Security 2022. Bellare and Hoang. Efficient schemes for committing authenticated encryption. EUROCRYPT 2022. Chan and Rogaway. On committing authenticated-encryption. ESORICS 2022. Orr Dunkelmann, Shibam Ghosh, and Eran Lambooij. Practical related-key forgery attacks on full-round TinyJAMBU-192/256. In ToSC 2023 (2), 2023. Dodis, Grubbs, Ristenpart, and Woodage. Fast message franking: From invisible salamanders to encryptment. CRYPTO 2018. Farshim, Libert, Paterson, and Quaglia. Robust Encryption, Revisited. PKC 2013. Farshim, Orlandi, and Ro ie. Security of symmetric primitives under incorrect usage of keys. In ToSC 2017(1), 2017. Len, Grubbs, and Ristenpart. Partitioning oracle attacks. USENIX Security 2021. Menda, Len, Grubbs, and Ristenpart. Context discovery and commitment attacks - how to break CCM, EAX, SIV, and more. EUROCRYPT 2023. Yusuke Naito, Yu Sasaki, and Takeshi Sugawara. Committing security of Ascon: Cryptanalysis on primitive and proof on mode. In ToSC 2023 (4), 2023. [BH22] [CR22] [DGL23] [DGRW18] [FLPQ13] [FOR17] [LGR21] [MLGR23] [NSS23]