Redundancy AES Masking for Secure Data Protection
AES, a widely-used encryption standard, is vulnerable to side-channel attacks. Discover how the RAMBAM approach enhances AES security by mapping data into a redundant domain and applying unique transformations. Learn about protection against attacks like SIFA and the significant advantages of employing redundancy in AES implementations.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
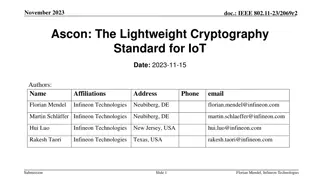
Redundancy AES Masking Basis for Attack Mitigation (RAMBAM) CHES 2022 September 20th, 2022 Leuven, Belgium
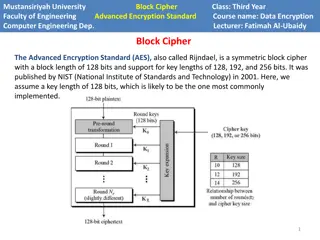
AES the State of the Art Among the design goals of the NIST AES competition (1997-2000) are: Computational efficiency Memory requirements AES is highly prone to SCA. Since 2000, many defenses of AES against SCA were suggested. Most were broken. TI, DOM, LMDPL provide protection (under certain assumptions). The combination of the protection against SCA with the original design goals has remained a challenge: TI and DOM inherently have high latency. LMDPL has low latency, but takes up a significant area and requires many random bits. Sep 20, 2002 Redundancy AES Masking Basis for Attack Mitigation (RAMBAM), CHES 2022, Leuven, BE 2
The RAMBAM Approach The bytes of the expanded key and of the data are randomly mapped into a redundant domain (8+d bits instead of 8 bits per byte). The AES transformations are performed in the redundant domain. The leakage decreases roughly exponentially as a function of the redundancy d. The variant with d=8 provides a high level of protection. Sep 20, 2002 Redundancy AES Masking Basis for Attack Mitigation (RAMBAM), CHES 2022, Leuven, BE 3
The AES Transformations in the Redundant Domain AddRoundKey remains a XOR. ShiftRows remains a permutation of bytes. MixColumns remains four multiplications by a 4*4 matrix. The matrix coefficients need to be represented in the polynomial basis of a root of P. SubBytes see the next slide Regular domain GF(2)[x]/P0 Redundant domain GF(2)[x]/PQ Change basis Bytes of key/data Bytes of key/data Add PR AES Reduce mod P Bytes of output Bytes of output Change basis Canonic Homorphism Sep 20, 2002 Redundancy AES Masking Basis for Attack Mitigation (RAMBAM), CHES 2022, Leuven, BE 4
Redundant SubBytes (S-box) Raising to the Power of 254 Pow2 Aff X14 X2 SubBytes(x) Pow4 X254 X3 X12 X Pow16 Mul2 Aff X15 X240 Mul2 SubBytes(x) The intermediate results are re-randomized by XORing with multiples of P. 7 d-bit coefficients of P are used, one for each stage of the inversion. Without re-randomization the leakage is significant. The same coefficients are reused for all the bytes and at all the rounds: 7 coefficients per 7 stages of the inversion The set of multiples of P is rotated by 1 at each clock cycle. The reuse of random bits is a significant practical advantage of RAMBAM. Sep 20, 2002 Redundancy AES Masking Basis for Attack Mitigation (RAMBAM), CHES 2022, Leuven, BE 5
Protection against Statistical Ineffective Fault Attack (SIFA) Similarly to the share-based schemes (TI, DOM), RAMBAM is inherently protected against SIFA1. The minimal number of simultaneously faulted bits in the state register necessary to extract usable information from SIFA depends on the redundancy. For redundancy 8 with P=0x139 or P=0x1d7, no attack with less than 5 simultaneously faulted bits can succeed. In the TI and DOM implementations the typical number of shares is less than 5, so there is a chance of a successful attack with 4 simultaneously faulted bits. In an independent vulnerability evaluation of RAMBAM (see below), both SIFA types SIFA1 and SIFA2 were unsuccessful. Sep 20, 2002 Redundancy AES Masking Basis for Attack Mitigation (RAMBAM), CHES 2022, Leuven, BE 6
Experimental Results the T-test as a Function of the Redundancy (1 S-box) Sep 20, 2002 Redundancy AES Masking Basis for Attack Mitigation (RAMBAM), CHES 2022, Leuven, BE 7
Experimental Results the T-test for Redundancy 8 (16 S-boxes) Sep 20, 2002 Redundancy AES Masking Basis for Attack Mitigation (RAMBAM), CHES 2022, Leuven, BE 8
Experimental Results - Summary The 1stand 2ndorder t-tests show no leakage (checked up to 5M traces for the 1-Sbox version, up to 384M traces for the 16-Sbox version). Latency of 12 clock cycles in the 16-Sbox version Unlike the TI/DOM approach (latency of 246 clock cycles in the fastest one) Can be decreased if the middle rounds are not protected Comparing with TI/DOM even in the compact version RAMBAM has a lower latency and a higher throughput-per-area ratio. Technology Area Maximal clock frequency Throughput / area Random bits per AES encryption RAMBAM 79 kGE 500 MHz @45nm 150 Mbps/kGE* 184 Sasdrich et al. CHES 2020 123 kGE 100 MHz @28nm 10 Mbps/kGE 5400 * Extrapolated to 28 nm, assuming frequency is roughly inversely proportional to the gate size of the chip technology Sep 20, 2002 Redundancy AES Masking Basis for Attack Mitigation (RAMBAM), CHES 2022, Leuven, BE 9
Vulnerability Evaluation by a Common Criteria Lab A vulnerability evaluation of RAMBAM in a configuration with d=8 was performed. The 1stand 2ndorder (univariate and multivariate) t-test analyses on over 30M traces showed no leakage. Template attacks using 15M traces at the profiling stage and 300K traces at the attack stage, found no bytes of the key. All attempts to attack using SIFA, both SIFA1 and SIFA2, were unsuccessful. Passed the evaluation at the Common Criteria AVA_VAN.5 level (corresponds to EAL7) Sep 20, 2002 Redundancy AES Masking Basis for Attack Mitigation (RAMBAM), CHES 2022, Leuven, BE 10
Conclusions RAMBAM is a practical algorithmic protection of AES against SCA and SIFA. High security along with high performance and low chip area are similar to those of many unprotected implementations. Low number of random bits used Many possible configurations: Compact version (1 Sbox) appropriate for IoT devices Fast versions (latency of 12 clock cycles per AES or lower) for ultra-high bandwidth encryption (hundreds of Gbps) There are also fast implementations in SW. Sep 20, 2002 Redundancy AES Masking Basis for Attack Mitigation (RAMBAM), CHES 2022, Leuven, BE 11
Thank you for your attention! Thank you for your attention!