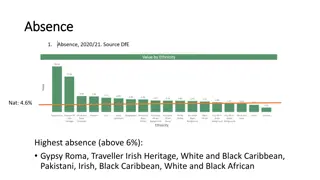
Safe Access to Data at University of Bristol
Introducing safe access to data at the University of Bristol, regarding the background, approach taken, unforeseen challenges, lessons learned, and future plans. The initiative includes the establishment of a Data Access Task & Finish Group and the implementation of recommendations to enhance data access levels and processes. The university has set up structured workflows and access levels for different types of data, ensuring secure and compliant data sharing practices."
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
Introducing Safe Access to Data at the University of Bristol Debra Hiom d.hiom@bristol.ac.uk and Kellie Snow kellie.snow@bristol.ac.uk 12thInternational Digital Curation Conference 21stFebruary 2017
Overview Background and approach taken Unforeseen challenges and lessons learned Future plans Advice for other institutions 2
Background Research Data Repository (data.bris) went live in July 2014 For open data only Immediately apparent some researchers would require restricted access Studies wanting to share, but not knowing how informal processes 3
Data Access Task & Finish Group Set up as result of report to University Research Ethics Committee in Nov 2014 Representation from RDS, IT services, Research Governance, Secretary s Office (DPA/FoI), Contracts, senior academics Met three times: Gain a better understanding of issues of data access and sharing in relation to sensitive data Assess and identify existing University processes Highlight where processes needed adapting or developing Many of proposed procedures based on EAGDA recommendations and UKDA 4
Data Access T&F Group recommendations October 2015 produced set of recommendations: Adoption of 4 standard data access levels Access levels embedded in ethics application process Consideration of data access levels at contracts stage Processes for handling restricted and controlled datasets piloted Use of a standard data access agreement for restricted and controlled datasets Setting up a permanent Data Access Committee: Ensure participant consent adhered to Oversee compliance with legal and regulatory requirements Assess any risks related to granting access e.g. re-identification 5
Data Access Levels Online and available to anyone without restriction. No sensitivities. Open Available to bona fide researchers. Repository staff will check request and credentials. Restricted Only available after panel of senior staff (DAC) have assessed request. Highly sensitive or older studies where appropriate permissions have not been sought. Controlled Data not available for sharing (except regulators) because of ethical, IPR, prior exclusive agreements or other constraints (requests handled by Information Rights Officer). Closed 7
At the start of a project Researcher identifies likely access level(s) that will be used Outlined in DMP Allocated as part of ethics application (where appropriate) Potential to include this in contracts with external partners 8
At the data deposit stage Researcher assigns access level in metadata record (verified by RDS) DOI landing page/repository record directs third party to RDS to request access form Dataset itself is stored either within Research Data Storage Facility or with research group 9
When a request is received Restricted Controlled 10
Training and Guidance Sensitive data guidance Short video Sensitive data Bootcamp Specialist workshop 11
Unforeseen challenges Procedure for checking if applicants bona fide Procedure and system for making and retaining Data Access decisions Storage location of datasets Supplying large datasets Some researchers may have their own governance processes 12
Future plans Software system to deal with requests process (audit trail) Online request form Data Access Agreement repurposed by existing studies Further procedures around commercial data (contract issues, IP) Further knowledge and procedures around clinical data (esp. NHS) where do sharing responsibilities lie? 13
Advice for other institutions Never underestimate time involved getting agreement across the institution for processes You re unlikely to have covered every eventuality be prepared to be reactive to new scenarios There may be challenges from researchers, therefore need to put in place an appeals process/escalation route to the DAC Process will allow you to build better relationships with other University services Your researchers will be grateful! 14
Thank you for listening! data-bris@bristol.ac.uk @databris 15