Security Challenges on Edge Computing for IoT Devices - Overview and Solutions
Edge computing is a critical technology for IoT devices, but it also presents security challenges. Learn about the architecture models, performance analysis, and security designs in this field. Explore the implications, advancements, and future research areas to tackle security issues effectively.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
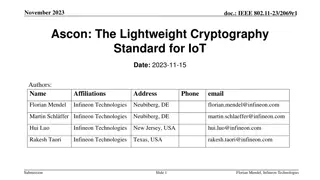
Topic Topic: Security challenges on Edge Computing for IoT devices Security challenges on Edge Computing for IoT devices Student Name: Krishna Prasad Pandey Student Name: Krishna Prasad Pandey Student Id: 11679258 Student Id: 11679258 Email: pandeykrishnaprasad0@gmail.com Email: pandeykrishnaprasad0@gmail.com blog:https://thinkspace.csu.edu.au/pandey11679258
Introduction Edge computing -Overview - Quality and Latency - Minimization of core network traffic - Scalability IoT devices - Smart devices - Sensors - Communication models
Lecture review 1: Researcher explained about the two-architecture model which are hierarchical model and software defined model. The performance of the IoT based devices are analysed and divides the section into architecture and its performance compared with latency, bandwidth, consume of energy and overhead. Along with computing edge devices, the edge computing help to reduce network latency and traffic through the user can get response easily in a real time. (Yu, W., Liang, F., He, X., Hatcher, W. G., Lu, C., Lin, J., & Yang, X. (2017). A survey on the edge computing for the Internet of Things. IEEE access, 6, 6900-6919.)
Lecture review 2: The research conducted purposed to increase network capabilities like smart cells, sensors and other gadgets based on IoT devices. The application used in smart cities, smart transportation, smart grid and smart signals are upgraded with edge computing through which the efficiency is increased. The new paradigm is established as the edge computing through which it helps to avoid problem related with network and to achieve maximum resources utilization (El-Sayed, H., Sankar, S., Prasad, M., Puthal, D., Gupta, A., Mohanty, M., & Lin, C. T. (2017). Edge of things: The big picture on the integration of edge, IoT and the cloud in a distributed computing environment. IEEE Access, 6, 1706-1717.)
Lecture review 3: Security design on this paper includes 3 architecture Edge- centric architecture Edge- based security architecture - User- centric - Device- centric - End to end security Edge-based authentication and authorization mechanisms (Sha, K., Yang, T. A., Wei, W., & Davari, S. (2020). A survey of edge computing- based designs for IoT security. Digital Communications and Networks, 6(2), 195-202.)
Open research issues Data quality for security - identify types of data - secure transmission Secure operating system - use of antivirus and backup Protocols for end device edge communications - implement BOYD security policies - use architecture like ShadowNet Genuine App - licence software - trusted vendor
Future directions To overcome weak credentials, use encryption on data transmission All the data stored and transmission should be tracked and monitored. Provide training for employee to remove technical risks Create team for quick response Use of digital identity for secure and authorized transaction Regular system update and upgrade
Conclusion In recent years, the challenge of securing IoT systems has sparked tremendous research interests. Emerging edge computing has resulted in many novel edge-based security designs for IoT security Cost of implementing is high, therefore high planning and security testing should be implemented Increased IoT devices leads to more challenge so security system should be update.
References: Goyal, S., Sharma, N., Kaushik, I., Bhushan, B., & Kumar, A. (2020). Precedence & Issues of IoT based on Edge Computing. In 2020 IEEE 9th International Conference on Communication Systems and Network Technologies (CSNT) (pp. 72-77). IEEE. Sha, K., Yang, T. A., Wei, W., & Davari, S. (2020). A survey of edge computing-based designs for IoT security. Digital Communications and Networks, 6(2), 195-202. El-Sayed, H., Sankar, S., Prasad, M., Puthal, D., Gupta, A., Mohanty, M., & Lin, C. T. (2017). Edge of things: The big picture on the integration of edge, IoT and the cloud in a distributed computing environment. IEEE Access, 6, 1706-1717.