Stack buffer overflow
A Stack Buffer Overflow occurs when a program writes more data to a buffer on the stack than what was initially allocated, leading to bugs, crashes, and potential security risks. This vulnerability can be exploited to execute arbitrary code on a protected machine. Learn about the causes, examples, and tools to prevent stack buffer overflows.
Uploaded on Feb 20, 2025 | 2 Views
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
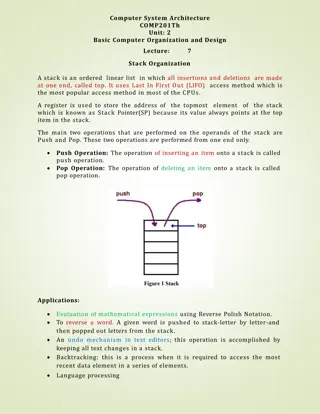
Stack buffer overflow http://en.wikipedia.org/wiki/Stack_buffer_overflow
What is a stack buffer overflow? Caused when a program writes more data to a buffer on the stack than what was initially allocated for the buffer Causes bugs, crashes, and can be used in an attack known as stack smashing (executing arbitrary code on a protected machine) Notable Example: Twilight Hack
#include <string.h> void foo (char *bar) { char c[12]; strcpy (c, bar); //no bound } int main (int argc, char **argv) { foo(argv[1]); }
Normal Execution hello is written to the char buffer. Note the null terminating byte. #include <string.h> void foo (char *bar) { char c[12]; strcpy (c, bar); //no bound } int main (int argc, char **argv) { foo(argv[1]); }
Buffer Overflow! Called with argument: AAAAAAAAAAAAAAAAAAAA\x08 \x35\xC0\x80 The return address now points to the start of the 12-byte buffer.
Lab 3 Due Friday April 22. Stack buffer overflow problem, very similar to what we have described today.