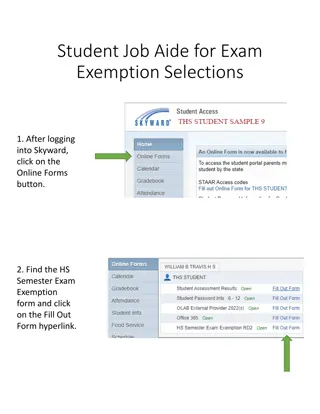
Types of Data Requests
The presentation "Types of Data Requests" by LDM Global outlines four primary categories of data requests encountered by organizations. Internal data requests originate within a company to support management, audits, and strategic planning. Externa
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
Types of Data Requests Presented by LDM Global
Internal Data Requests Initiated within an organization Common examples: Reports for management Data analysis for internal audits Focus on operational improvements and strategy planning Requires coordination across departments (IT, Legal, HR, Finance)
External Data Requests Initiated by external parties such as clients, vendors, or partners Common examples: Client due diligence Vendor assessments Data sharing governed by agreements (NDAs, contracts) Emphasis on accuracy, speed, and confidentiality
Legal and Compliance Data Requests Driven by regulatory and legal obligations Types include: eDiscovery requests Government or law enforcement subpoenas Requires strict adherence to compliance standards (e.g., GDPR, HIPAA) Often involves legal counsel and risk management teams
Freedom of Information (FOIA) Requests Public right to request information from government bodies Applies mainly to public sector organizations Requires: Timely response Transparency Redaction of sensitive information where necessary Promotes accountability and public trust