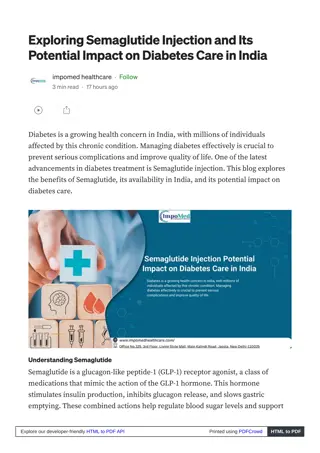
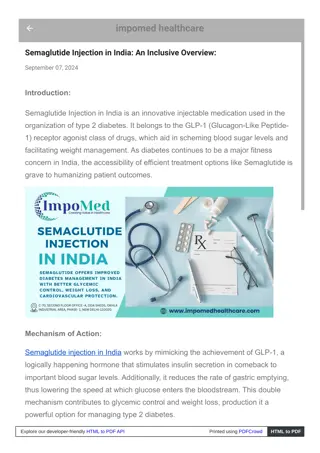
Understanding Early Bird APC Injection Technique
Learn about the Early Bird APC Injection technique, which involves hijacking legitimate processes to execute malicious shellcode before detection. Discover its basic concepts, mechanisms, advantages like camouflage and security hook bypass, as well as disadvantages like detection risks. Explore this advanced cybersecurity method for evading anti-malware detection.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
Early Bird APC Injection Achieving Camouflage by Hijacking a Legitimate Process before It hits Entry Point
Basic Concepts A malware creates a legitimate process in a suspended state Then, injects shellcode into it And inserts a job into the threads APC Queue And finally resumes the thread The shellcode executes before the process begins, to avoid detection by Anti-malware hooks
Mechanism of Early Bird APC Injection Target Process 1. Creates a Process in a Suspended State Malware Trojan Thread 2. Allocate Memory VirtualAllocEx APC Queue Shellcode 3. Copy Shellcode to Memory WriteProcessMemory 4. Add job to Queue QueueUserAPC Shellcode 5. Resumes Thread ResumeThread Allocated Memory Shellcode
Advantages & Disadvantages Of Early Bird APC Injection
Advantages Camouflages the execution of the malicious shellcode by hijacking a legitimate process before it hits entry point The remaining code of the actual legitimate process is abandoned whilst the shellcode runs Bypasses security product hooks. The shellcode executes before the process begins to avoid detection by Anti-malware hooks Runs with application icon of the original process.
Disadvantages Uses VirtualAllocEx and WriteProcessMemory, which are usually detected by AV unless obfuscated May occasionally crash upon exit