Understanding Information Security: Carving the Cybersecurity Landscape
Delve into the complex realm of information security by exploring various aspects, from attack domains to user privileges, networking, and security vocabulary. Build a foundational understanding to navigate the challenges of safeguarding digital assets effectively.
Uploaded on | 1 Views
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
Introduction to Information Security We looked at the heterogeneity and vastness of the topic of cyber-security, so where do we start, how do we carve it up?
the end-to-end backdrop while you are computing / using your computer split into attack domains users (humans) their computing environment (workstation) bits & pieces which make up their local area network the connection from lan to wan the wan accessing the protected campus environment from home (remote access)
vocabulary programs running on a single computer regular programs (man(1)) A program like others, but it uses the network: - socket - daemon USER LEVEL PROGRAMS NETWORK SERVERS: provide service to remove client programs (e.g., web server; database management system) User programs Running with non- admin privileges (e.g., Word processors) System programs Running with admin (or root) privileges: E.g., msconfig.sys; useradd Operating system, also man(2) OPERATING SYSTEM KERNEL: programs running with kernel (RING 0) privileges. Examples: Device drivers; DLLs (dynamic linked libraries) and loadable kernel modules (in UNIX/Linux). on a given computer
vocabulary Networking & Security The need for security- computing or communicating in the presence of adversaries. These days it is taken to mean a network of computing devices dealing in digitized information A high level way to think about it all starts with vocabulary
vocabulary 1. How it should work 1.Policy 2.Threat model 3.Mechanism 2. A model of the bad guys 3. software/hardware/tools to help
vocabulary 1 - Policy Policy the goals you wish to achieve what I want my system to be able to do only I can change the file with grades
vocabulary security policy What activities or events should be prevented/detected? Who are the actors or participants (maybe in terms of their roles) ? Give/withhold permission on classes/instances of object
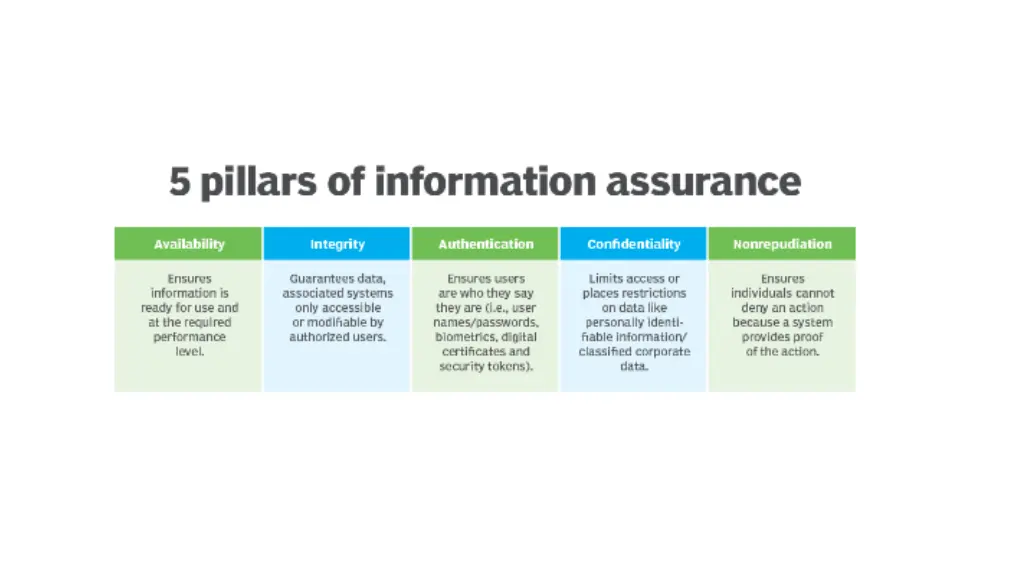
vocabulary security policy (the hackneyed cia acronym) security policies try to achieve C Confidentiality: information should not be disclosed to unauthorized parties I Integrity: information should not be modified in an unauthorized manner A Availabile: system or resource shall be available for use as intended
vocabulary security policy In practice computer systems are often compromised break-ins are pretty commonplace Build a file system make sure I can access the student information check - yep, I can access it
vocabulary security policy But in the negative form: AND nobody else can access it That s a much harder problem what can a unknown, potentially infinite set of attackers do? you can t prove a negative (false, but also pretty close to true)
vocabulary security policy Also note: achieving desired behavior vs preventing undesired behavior Different way of thinking, especially during design
vocabulary security policy The right set of assumptions is not so easy They are laid down over time like a sedimentary rock via iterative process after each failure
vocabulary Threat Model 2. Threat model Threat model a set of assumptions about the bad guy if the bad guy is omniscient, you can t get anywhere bad guy does not have my password, or my laptop, or keys Not that easy to articulate in a precise way
vocabulary Threat Model Who is your enemy? What do they know? What do they have?
vocabulary Mechanism 3. Mechanism 3. Mechanism stuff that will let us achieve our goals under the assumptions (stuff = mostly software and hardware)
vocabulary Mechanism A security mechanism/control a component, technique, or method for attempting to implement a security policy. WAF Web Application Firewall (or maybe When the Application Fails)
vocabulary Mechanism Security mechanisms are typically about Prevention don t let anyone break the policy (software for file permission check) Detection/Recovery : detect when policy is violated, maybe fix it (ids, packet sniffers looking for patterns) User authentication (vs user identification) (cryptographic hash functions, encryption software)
vocabulary Mechanisms Security mechanisms may involve: Identification of principals (e.g. user name ) Authentication of principals (e.g. password, biometric) Authorization: checking to see if principal is authorized for requested action Physical protection: locks, enclosures Logical protection: correct software
Whats the difference? identify me authenticate me authorize me
Policy gone wrong Policy - you must know the password to log in Password recovery we ll email you a link to reset it answer these security questions to reset it
security policy But now I changed the log-in policy to know the password, or know the answers to these questions, or have access to the backup email
Threat Model gone wrong Threat models that assume secure human behavior and/or specific adversary behavior A 56 bit DES key is enough, only we here at the NSA have the computing power to search that space Look what I got for Christmas!
Organizational checkpoint What does the field of cybersecurity cover? What does the acronym CIA stand for, and why do/don t we use it? What is a Security Policy? What is a Threat Model? What does Mechanism mean in this context? What are the differences between authentication, authorization, and identification?
