Understanding the Feistel Cipher Structure for Network Security
Explore the Feistel Cipher structure, objectives, and encryption process for enhancing network security. Learn how data is encrypted and decrypted using this symmetric block encryption algorithm developed by Horst Feistel. Adapted from "Network Security Essentials: Applications and Standards" by William Stallings.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
Feistel Cipher Structure Network Security 1
Feistel Cipher Structure Objectives of the Topic After completing this topic, a student will be able to explain structure of Feistel Cipher. 2
Feistel Cipher Structure Figures and material in this topic have been adapted from Network Security Essentials: Applications and Standards , 2014, by William Stallings. 3
Feistel Cipher Structure Many symmetric block encryption algorithms have a structure, which was first described by Horst Feistel of IBM in 1973. 4
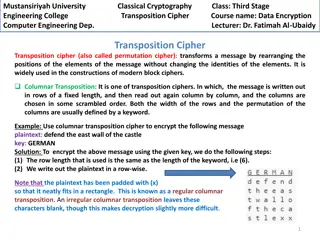
Feistel Cipher Structure Feistel Encryption The inputs to the encryption algorithm are a plaintext block of length 2w bits and a key K. The plaintext block is divided into two halves, LE0 and RE0. 5
Feistel Cipher Structure The two halves of the data pass through n rounds of processing and then combine to produce the ciphertext block. 6
Feistel Cipher Structure Each round i has as inputs LEi -1 and REi -1 derived from the previous round, as well as a subkey Ki derived from the overall K. 7
Feistel Cipher Structure In general, the subkeys Ki are different from K and from each other and are generated from the key by a subkey generation algorithm. 8
Feistel Cipher Structure In a given round, a substitution is performed on the left half of the data. Apply a round function F to the right half of the data and then take XOR of the output of that function and the left half of the data. 9
Feistel Cipher Structure The round function has the same general structure for each round but is parameterized by the round subkey Ki. A permutation is then performed to interchange the two halves of the data. 10
Feistel Cipher Structure Feistel Encryption 16 rounds 11
Feistel Cipher Structure Feistel Decryption Use the ciphertext as input to the algorithm, but use the subkeys Ki in reverse order. That is, use Kn in the first round, Kn-1 in the second round, and so on until K1 is used in the last round. 12
Feistel Cipher Structure Feistel Decryption 13
Feistel Cipher Structure Encryption Decryption 14
Feistel Cipher Structure Feistel Cipher Design Features: Block size: Larger block sizes mean greater security (all other things being equal) but reduced encryption/decryption speed. 15
Feistel Cipher Structure Key size: Larger key size means greater security but may decrease encryption/decryption speed. 16
Feistel Cipher Structure Number of rounds: The essence of a symmetric block cipher is that a single round offers inadequate security but that multiple rounds offer increasing security. 17
Feistel Cipher Structure Subkey generation algorithm: Greater complexity in this algorithm should lead to greater difficulty of cryptanalysis. Round function: Greater complexity generally means greater resistance to cryptanalysis. 18
Feistel Cipher Structure Fast software Algorithms: Encryption is embedded in applications or utility functions in such a way as to preclude a hardware implementation. Thus, speed of execution of the algorithm becomes a concern. 19
Feistel Cipher Structure Ease of analysis: If the algorithm can be concisely and clearly explained, it is easier to analyze that algorithm for cryptanalytic vulnerabilities and develop a higher level of assurance as to its strength. End 20