Welcome to Mrs. Greenhouse's Classroom
Welcome to Mrs. Greenhouse's classroom where students are encouraged to follow classroom rules, show respect, and work together as a family. The guidelines in the classroom include raising hands for attention, using manners when speaking to adults, maintaining cleanliness, and being punctual. Students are reminded to keep voices low, follow procedures, and sharpen pencils in preparation for the next day. The emphasis is on creating a positive learning environment where everyone can thrive and have a fantastic school year.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
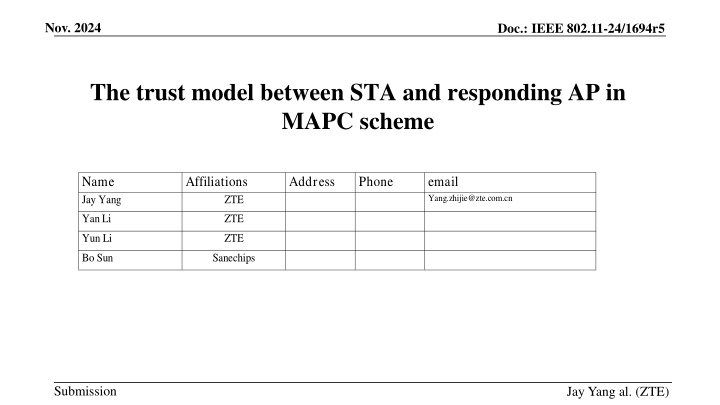
Nov. 2024 Doc.: IEEE 802.11-24/1694r5 The trust model between STA and responding AP in MAPC scheme Name Jay Yang Affiliations Address Phone email Yang.zhijie@zte.com.cn ZTE YanLi ZTE Yun Li ZTE Bo Sun Sanechips Submission Jay Yang al. (ZTE)
Nov. 2024 Doc.: IEEE 802.11-24/1694r5 Introduction In Co-BF,11bn agreed on two new sounding sequences: Joint sounding and sequential sounding. In Joint and cross-BSS sequential sounding, the responding AP need to overhear the CSI frame transmitted by the unassociated STA. Meanwhile, the 3rd party also can overhear the unprotected CSI frame, and then sense the end-user activity between STA and it s associated AP, which will bring some user privacy issue. In this contribution, we would like to discuss the CSI protection between STA and responding AP. Submission Slide 2 Jay Yang, et al. (ZTE)
Nov. 2024 Doc.: IEEE 802.11-24/1694r5 Recap: CSI protection in 802.11bi SPEC(baseline of 802.11bn) The latest 11bi draft defines the protected CSI frame between AP and its associated STA. Before 11bi, the 3rd party may overhear the plain text of CSI frame, and then sense the end user activity between AP and the associated STA. In the latest 11bi draft,the individual addressed CSI frame is encrypted by the PTK,and thus the user privacy is enhanced. Submission Slide 3 Jay Yang, et al. (ZTE)
Nov. 2024 Doc.: IEEE 802.11-24/1694r5 Problem state and Motivation CSI protection defined by TGbi conflicts with the overhearing mechanism in sounding procedure proposed by TGbn Overhearing by the responding AP in Co-BF sounding is a promising function and is widely discussed in 11bn group. But the responding AP can t decode the overheard CSI frame once it s encrypted. Conclusion: The encrypted CSI frame causes overhearing mechanism become useless. Motivation We propose to define a new protected CSI mechanism between STA and responding AP in Co-BF sounding procedure to address the collision issue above. Submission Slide 4 Jay Yang, et al. (ZTE)
Nov. 2024 The mainly procedures of group addressed protected CSI frame Doc.: IEEE 802.11-24/1694r5 1) The initiating AP shares a separated group key(GK) to all the associated STAs. 2) The imitating AP share the GK to the responding APs that participates Co-BF procedure. 3) STA sends the encrypted CSI frame in a group addressed manner in Cross-BSS sequential and/or Joint sounding procedure. To avoid the PN reuse issue, the initiating AP may: Assign partial PN space to each STA(e.g. a different MSB 24-bit assigns to one STA), and each STA manages it s own LSB 24-bits(increment the PN after sending a encrypted CSI frame) Assign an increasing PN in ICF or BFRP in each sounding procedure, and STA encrypted the CSI frame via the assigned PN and GK. Slide 5 Submission Jay Yang, et al. (ZTE)
Nov. 2024 The following figure depicts an example of GK sharing and CSI encryption with the shared GK in Joint sounding procedure Doc.: IEEE 802.11-24/1694r5 Submission Slide 6 Jay Yang, et al. (ZTE)
Nov. 2024 The comparison of the proposed CSI protection between STA and responding AP Opt1: PTK Sharing between initiating AP and responding AP Pons: Individual addressed protected CSI frame can be reused,e.g. STA sends the protected CSI frame to the initiating AP, and the responding AP can overhear the CSI and decode it with the shared PTK. Cons: The single PTK is used in both MGMT. and data frame, the responding AP also can decode the overheard data frame exchange between STA and its associated AP, which causes additional user privacy concern. Doc.: IEEE 802.11-24/1694r5 Opt2: PTK negotiation between STA and responding AP Pons: Compared with the PTK Sharing approach, the user privacy concern can be mitigated. e.g. the STA encrypts the CSI frame via a separated PTK, which is negotiated between STA and responding AP. Cons: It only wok on cross-BSS sequential sounding procedure. That s, such solution can t be applied in Joint sounding procedure. Opt3(Preferred): GK Sharing between initiating AP and responding AP Pons: Compatible with both cross-BSS Sequential sounding and Joint sounding procedure. Cons: No. Submission Slide 7 Jay Yang, et al. (ZTE)
Nov. 2024 Doc.: IEEE 802.11-24/1694r5 Summary Analyze the conflict issue between the protected CSI frame and overhearing mechanism. Compare all possible solutions and propose to the define the group addressed and protected CSI frame Compared with PTK sharing and PTK negotiation mechanism, a separated GTK sharing can be applied in both sequential sounding and Joint sounding procedure, and also it mitigates the end-user privacy concern. Propose a general procedure of GTK sharing for CSI protection including the PN assignment. Submission Slide 8 Jay Yang, et al. (ZTE)
Nov. 2024 Doc.: IEEE 802.11-24/1694r5 THANK YOU Submission
Nov. 2024 Doc.: IEEE 802.11-24/1694r5 Reference 1. 20/0123r0 Channel Sounding for Multi-AP CBF 2. 24/1542r0 Sounding Schemes for Coordinated Beamforming 3. 24/209r5 Specification Framework for TGbn 4. 24/1823r0 CSI in Sounding in CBF 5. 802.11bi draft 1.0 Submission Slide 10 Jay Yang, et al. (ZTE)
Nov. 2024 Doc.: IEEE 802.11-24/1694r5 SP1 Do you agree to have a mechanism to protect the CSI frame between STA and responding AP in sequential sounding and Joint sounding procedure? Submission Slide 11 Jay Yang, et al. (ZTE)
Nov. 2024 Doc.: IEEE 802.11-24/1694r5 Appendix: Sequential sounding in motion[#100] Submission Slide 12 Jay Yang, et al. (ZTE)
Nov. 2024 Doc.: IEEE 802.11-24/1694r5 Appendix: Joint sounding sequence in motion[#101] Submission Slide 13 Jay Yang, et al. (ZTE)