Understanding Kerberos for Network Security
Kerberos is a key distribution and user authentication service developed at MIT for secure communication in distributed environments. It addresses threats such as impersonation, network address alterations, and eavesdropping, ensuring secure access to authorized users and services on a network.
Uploaded on | 0 Views
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
What is Kerberos? Network Security 1
What is Kerberos? Objectives of the Topic After completing this topic, a student will be able to explain Kerberos. 2
What is Kerberos? Figures and material in this topic have been adapted from Network Security Essentials: Applications and Standards , 2014 by William Stalling. 3
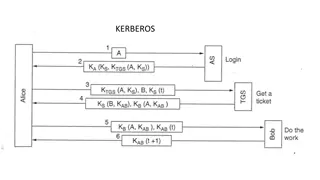
What is Kerberos? Kerberos is a key distribution and user authentication service developed at MIT as part of Project Athena. 4
What is Kerberos? The problem that Kerberos addresses is this: Assume an open distributed environment in which users at workstations wish to access services on servers distributed throughout network. 5
What is Kerberos? We would like for servers to be able to restrict access to authorized users and to be able to authenticate requests for service. A workstation cannot be trusted to identify its users correctly to network services. 6
What is Kerberos? In particular, the following three threats exist: 1. A user may gain access to a particular workstation and pretend to be another user operating from that workstation. 7
What is Kerberos? 2. A user may alter the network address of a workstation so that the requests sent from the altered workstation appear to come from the impersonated workstation. 8
What is Kerberos? 3. A user may eavesdrop on exchanges and use a replay attack to gain entrance to a server or to disrupt operations. 9
What is Kerberos? In any of these cases, an unauthorized user may be able to gain access to services and data that he or she is not authorized to access. 10
What is Kerberos? Rather than building elaborate authentication protocols at each server, Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. 11
What is Kerberos? Kerberos relies exclusively on symmetric encryption, making no use of public-key encryption. 12
What is Kerberos? Motivation If a set of users is provided with dedicated personal computers that have no network connections, then a user s resources and files can be protected by physically securing each computer. 13
What is Kerberos? When these users instead are served by a centralized time- sharing system, the time-sharing operating system can enforce access-control policies based on user identity and use the logon procedure to identify users. 14
What is Kerberos? More common is a distributed architecture consisting of dedicated users (clients) and distributed or centralized servers. 15
What is Kerberos? In this environment, there are three approaches to security. 16
What is Kerberos? 1. Rely on each individual client workstation to assure the identity of its user or users and rely on each server to enforce a security policy based on user identification (ID). 17
What is Kerberos? 2. Require that client systems authenticate themselves to servers, but trust the client system concerning the identity of its user. 18
What is Kerberos? 3. Require the user to prove his or her identity for each service invoked. Also require that servers prove their identity to clients. 19
What is Kerberos? In a small, closed environment in which all systems are owned and operated by a single organization, the first or perhaps the second strategy may suffice. 20
What is Kerberos? In a more open environment in which network connections to other machines are supported, the third approach is needed to protect user information and resources housed at the server. 21
What is Kerberos? Kerberos supports this third approach. Kerberos assumes a distributed client/server architecture and employs one or more Kerberos servers to provide an authentication service. End 22